https://fedoramagazine.org/gnupg-a-fedora-primer


GPG, or GnuPG, refers to the Gnu Privacy Guard utility. GPG is a freely available implementation of the OpenPGP
standard that was released by Werner Koch in 1999. The security and
privacy of data and individuals is an important topic in modern
culture. The OpenPGP standard allows GPG and other applications to work
together to secure and protect your data.
This series will explain the basic fundamentals of GPG and take you step by step through using it. The OpenPGP standard includes the basic features of confidentiality, integrity, and non-repudiation. By supporting this standard, GPG provides all three features.
The example plaintext below is encrypted with the pass phrase “openme”. This is an example of a symmetric algorithm, where the same key is used for both encryption and decryption.
This series will explain the basic fundamentals of GPG and take you step by step through using it. The OpenPGP standard includes the basic features of confidentiality, integrity, and non-repudiation. By supporting this standard, GPG provides all three features.
Confidentiality
Confidentiality is the ability to keep contents of a file or message private. To provide confidentiality, GPG can convert the original contents of a file, called plaintext, to an encrypted version called ciphertext. This can help keep your files secure on a computer, removable drives, or when transmitted over the Internet. Think of it as using a secret code to write a letter. Even if the letter is intercepted and the envelope steamed open, the message cannot be read.The example plaintext below is encrypted with the pass phrase “openme”. This is an example of a symmetric algorithm, where the same key is used for both encryption and decryption.
Plain text: the quick brown fox
Encrypted text: jA0EBwMCqQso2Gtwdw9g0k0B+60qwezrj/6rR3KXt/ckSHtqr0jt2feIKKRV+Qwt HnsVUOu51Amd9pE1xR0WE75GQjWfwEN9P34Z1HkP0pVyDOGKme06AJDL6W8uRA== =/YrsA future article in this series will cover email encryption with GPG.
Integrity
Another function of GPG ensures the integrity
of a file. This feature is used by the Fedora Project to help ensure
the image you download is the one Fedora provides. In the case of
Fedora, both a checksum and a signature are generated.
A checksum is a set of digits that represent data, such as a file.
The checksum is generated by a special one-way mathematical algorithm.
The algorithm cannot be reversed to discover the original data from the
checksum. The algorithm is also designed
to make it exceedingly difficult for two sets of data to generate the
same checksum.
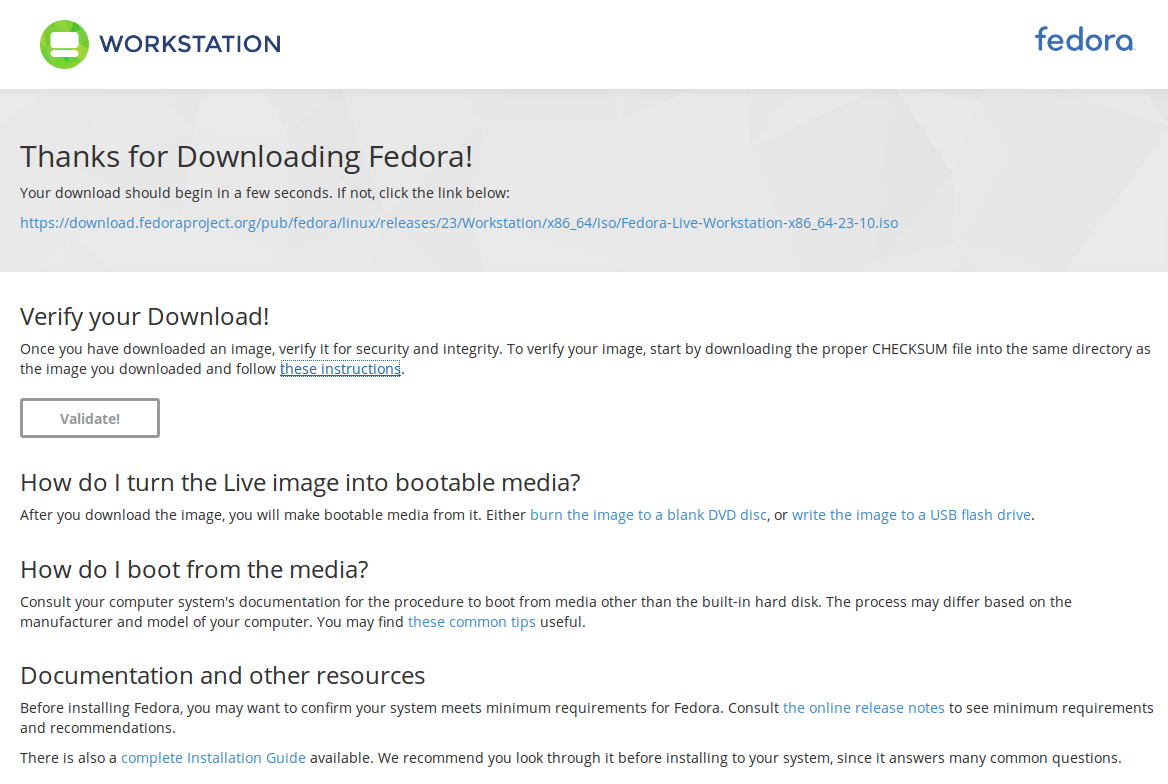
You will see this on the page that thanks you for downloading Fedora:
The text below is from the page you see when you click the Validate button on the page above. To verify this information and the image itself, follow the link for the instructions.
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA256 # The image checksum(s) are generated with sha256sum. SHA256 (Fedora-Workstation-netinst-x86_64-23.iso) = f38d1aca6211b6bbb2873a550f393d03866294e3e5094256feb4cd647c25a310 SHA256 (Fedora-Live-Workstation-x86_64-23-10.iso) = a91eca2492ac84909953ef27040f9b61d8525f7ec5e89f6430319f49f9f823fe -----BEGIN PGP SIGNATURE----- Version: GnuPG v1 iQIcBAEBCAAGBQJWM9N7AAoJEDJHTPg07Jy6vLQP/2m9NYWcPo8cIZDw7fq+u5LC g50R+8TQlY76LMzv0NAuIsx6pw3JW/BZSRVd74Jlg+cPK6te9XVmJ2HS9WoSWvPw T821eRRbV8ou3JthST/ZPbcdy1L3Qz6Xbfu1u7LwE4yjgh+8fQJ7ZKANpchEuOhk j9JK45vwbgUj9gWSQghoe+2dXOtTmtJAnPjTirYmeB0JJubwjEgT+O9y+EaUXABs oKTUH2ej6qsLSWjbjcH3bxjaQwvzZKEN3KgKyFIBpIdeCVMp/JiLqHwQ8Fqtwsu9 j2sv7oB+arE/RjOprgC6TDgbx753zoFmHo0maiCMCCFfSDsea8pHay3n7u/Exr/8 8XE9UFXRMnFPFmdY21uE8SIilnE/Ig3BAqCIo2qN/8gx6bEAIaC10B+h7gtS2D46 J5982pneqyw88MCLUIN27kx59vTr9N6DNPomz5VEgf2J7rmfE3ZbrIS45r2zJPjt sbr6mjmJrx+sPWx5Ie0pgkjMbgQeZ8yN4GegyJwwhjRIoYZl3W7QyAaYJbKRfFPP hn+oOoe3RB8Jhhoma29MezDesL9t8wafmPelp5sNU02ORvuhvwcpKdmPyku0VzI+ PuYzDB19DCNjHV3UKMQ2BlR6m1AevCtra/WDqeXliwFWGT//iQjIBMwB4o2byxFe R3cfguVlycgsPAIPKhKW =Jvm2 -----END PGP SIGNATURE-----
The signature also provides integrity
checking for the checksums. If the checksum values were to change, the
signature would no longer match. After verifying the signature, the hash
values can be used to compare to a checksum on the downloaded image
file. If they are the same, you can be certain the image is not tampered
with or corrupted.
Non-repudiation
Non-repudiation ensures that a
person cannot deny signing a file or message. If you always sign your
messages, someone receiving an unsigned message should suspect it is a
fake. The non-repudiation process requires a more complex
cryptographic system than the symmetric example shown earlier. Asymmetric or public-key cryptography makes this feature possible.
In a public-key system, each user has a public key, which they share as widely as possible; and a private key, which they protect as carefully as possible. Keyservers on the internet can collect and advertise public keys to make exchange of information easier.
To know if a signature is valid requires
use of a keyserver to retrieve the public key for that signature.
However, downloading or having a public key labeled as owned by someone
does not prove the key actually belongs to that person.
For this reason, keys must be verified
personally to be trusted. If you meet someone in person and verify their
identity, you can trust their key. This “web of trust,” which will be
discussed later in the series, allows you to trust a key from a person
you haven’t personally met.
Authenticity
When confidentiality, integrity and non-repudiation are combined, authenticity
is achieved. A file or message can be kept secret, verified to not have
been tampered with, and verified to come from the specified source.
This is the beginning of a series of
articles about using GPG. This series will show you how to create and
maintain keys with GPG, understand and use the web of trust, understand
and run key signing events, use GPG with email, and encrypt and sign
files.