https://www.howtoforge.com/linux-cut-command
In Linux, if you want to print a file's content on stdout, the first command that comes to mind is cat. However, there may be times when the requirement is to remove certain part of the file and print only the rest of the content. You'll be glad to know there exists a tool - dubbed cut - that lets you do this.
In this article, we will discuss this tool using some easy to
understand examples. But before we do that, it's worth mentioning that
all examples in this article have been tested on an Ubuntu 18.04 LTS
machine.
For example, suppose there's a file named file1.txt that contains the following line:
For example, the following command will make sure that all bytes including and after the one at number 5 are displayed.
For example, ♣ is a special character that occupies multiple bytes. So if you want to use the cut command on a text stream that contains these kind of characters, then it's better to use -c instead of -b. Functionality wise, both -c and -b work in similar way.
For example, suppose the input file contains comma-separated fields:
In Linux, if you want to print a file's content on stdout, the first command that comes to mind is cat. However, there may be times when the requirement is to remove certain part of the file and print only the rest of the content. You'll be glad to know there exists a tool - dubbed cut - that lets you do this.
Linux cut command
The cut command in Linux lets users remove sections from each line of files. Following is its syntax:
cut OPTION... [FILE]...
Here's what the man page says about this utility:Print selected parts of lines from each FILE to standard output. With no FILE, or when FILE is -, read standard input.And following are some Q&A-styled examples that should give you a good idea on how this utility works.
Q1. How to use the cut command?
The cut command expects user to provide a list of bytes, characters, or fields. You can provide bytes using the -b command line option.For example, suppose there's a file named file1.txt that contains the following line:
abcdefghijklmnopqrstuvwxyzAnd you want to only display the first three bytes. Then in this case, you can use the -b option in the following way:
cut file1.txt -b1,2,3
The output will be:abcYou can also specify a range:
cut file1.txt -b1-10
Following is the output produced in this case:abcdefghijMoving on, you can also use hyphen (-) with a number to tell the cut command to either display all bytes after the byte at that number or all bytes before the byte at that number.
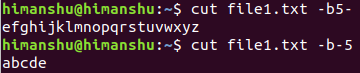
For example, the following command will make sure that all bytes including and after the one at number 5 are displayed.
cut file1.txt -b5-
And the following command will display the first 5 bytes:
cut file1.txt -b-5
Q2. How to deal with characters?
Sometimes, the file you pass to the cut command contains characters that are more than one byte in size. In that case, it's advisable to use the -c option which lets the tool correctly understand which characters you want to display or remove.For example, ♣ is a special character that occupies multiple bytes. So if you want to use the cut command on a text stream that contains these kind of characters, then it's better to use -c instead of -b. Functionality wise, both -c and -b work in similar way.
Q3. How cut works with delimiters?
You can also make the cut command work with delimiters. For this, you can use the -d command line option.For example, suppose the input file contains comma-separated fields:
Howtoforge, HTF, howtoforge.com
FaqForge, FF, faqforge.com
And you want only first and third entries, then this can be done in the following way:FaqForge, FF, faqforge.com
cut file1.txt -d, -f1,3
Note that the -f option lets you choose the fields you wanna display.