https://www.howtoforge.com/tutorial/openssh-security-best-practices
SSH (Secure Shell) is a cryptographic network protocol for initiating
text-based shell sessions on remote machines in a secure way.
OpenSSH is the standard SSH client and server used by most Linux Distributions. It is a connectivity tool that most administrators rely on to work on their Linux and *BSD servers. OpenSSH encrypts all traffic (including passwords) to effectively eliminate eavesdropping, connection hijacking, and other attacks. So in other word "OpenSSH ensures that the connection to your server is secure". See Wikipedia article for a detailed excurse on SSH.
This tutorial covers the best pratices to configure your SSH server securely.
Please choose a port that is not in use on your server yet. You can get a list of ports that are currently in use with the command:
After you set "PermitRootLogin" to "no", you can not login with root account anymore, although you use correct password for root user.
in /etc/ssh/sshd_config to limit SSH access to these users.
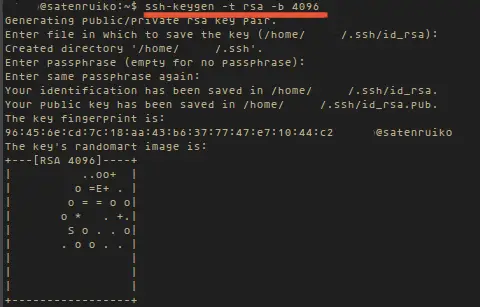
You can create the public / private key pair with this command:
Now upload the public key id_rsa.pub to your server with ssh-copy-id command.
Now go back to your server and edit your ssh file configuarion again.
and finally restart your ssh server :
OpenSSH is the standard SSH client and server used by most Linux Distributions. It is a connectivity tool that most administrators rely on to work on their Linux and *BSD servers. OpenSSH encrypts all traffic (including passwords) to effectively eliminate eavesdropping, connection hijacking, and other attacks. So in other word "OpenSSH ensures that the connection to your server is secure". See Wikipedia article for a detailed excurse on SSH.
OpenSSH Security
These are the six most important tasks to secure your SSH server setup:- Use a strong password.
- Change the SSH default port.
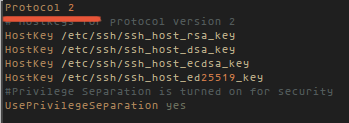
- Always use protocol version 2.
- Disable the root login.
- Limit user access.
- Use key-based for authentication.
Use a strong password
A password is a word or string of characters used for user authentication to prove identity or access approval to gain access to a resource. Keep it secret from those that are not allowed to access the server. Use a complex and long password, it should be easy to remember and unique according to you but not easy to guess for others. Don't use `admin123` or `admin` etc. that are easy to guess and dont use birthdays, name of your wife etc. A good password should also contain special chars lik '.!;/' (not just the characters a-c and 0-9). Use upper- and lower case characters in the password.Change the SSH default port
The default Post of the SSH service is 22, you should change that to make it less obvious that your server is running a SSH service. The SSH configuration file is located in /etc/sshd/ directory, you have to edit the config file /etc/ssh/sshd_config .
nano /etc/ssh/sshd_config
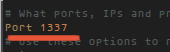
Search for the "Port" line:Port 22and change it to your favorite port number, example : 1337
Port 1337

Please choose a port that is not in use on your server yet. You can get a list of ports that are currently in use with the command:
netstat -ntap
This command results in a quite long list that shows all open ports
and connections. If you just like to check if your desired port is
available, use this command instead:
netstat -ntap | grep 4422
In this example I'll check if port 4422 is free. If the command does
not return a result, then the port is available and can be used for SSH.Always use protocol 2
SSH has two protocol versions, the old protocol 1 which is insecure and the new protocol 2. So Always use protocol 2 for your ssh server, it is more secure than protocol 1. More Info Here.
Disable root login
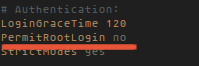
You should disable the direct login for the root user because there are many brute force attacks against the name of the root superuser. IMPORTANT: test the SSH login with your alternate non-root user that you plan to use for ssh logins before you disable the root account.PermitRootLogin no

After you set "PermitRootLogin" to "no", you can not login with root account anymore, although you use correct password for root user.
Limit user
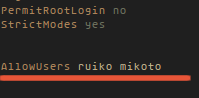
You should add a new user for login to your server. Assume that you have created the users ruiko and mikoto to login to your server, then you can add the new line :AllowUsers ruiko mikoto

in /etc/ssh/sshd_config to limit SSH access to these users.
Use Key Based Authentication
I recomended you to use this option, because this is very easy to setup and more secure then password based authentication. First you have to create a public private key paid on your local (desktop) computer, I use Linux to create it.You can create the public / private key pair with this command:
ssh-keygen -t rsa -b 4096
It will create 2 files located in ~/.ssh/ directory, id_rsa as private key and id_rsa.pub as public key. If it prompts for a password, you can leave it blank or type to your password. Using a password to protect your key is recommended.
Now upload the public key id_rsa.pub to your server with ssh-copy-id command.
ssh-copy-id -i ~/.ssh/id_rsa.pub user@serverip
It will automatically write your public key to the file ~/.ssh/authorized_keys/ in your server.Now go back to your server and edit your ssh file configuarion again.
nano /etc/ssh/sshd_config
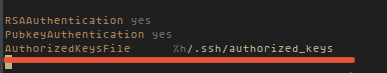
Uncomment this line:AuthorizedKeysFile %h/.ssh/authorized_keys

and finally restart your ssh server :
systemctl restart sshd
Now try connect to your server :
ssh -p '4422' 'user@serverIP'

No comments:
Post a Comment