https://www.blackmoreops.com/2016/10/17/browse-anonymously-in-kali-linux-with-anonsurf
IP spoofing, also known as IP address forgery or a host file hijack, is a hijacking technique in which a cracker masquerades as a trusted host to conceal his identity, spoof a Web site, hijack browsers, or gain access to a network. We use various methods to spoof our IP addresses, most common being using Proxy, VPN and TOR. I
found this interesting tool named Anonsurf and it will anonymize the
entire system under TOR using IPTables. It will also allow you to start
and stop i2p as well. That means you can browse anonymously in Kali
Linux with Anonsurf running in the background. Anonsurf will run and
keep changing IP address every so often or you can simply restart the
process to make it grab a new IP address and thus spoofing your own IP
address. Sounds good?
I
found this interesting tool named Anonsurf and it will anonymize the
entire system under TOR using IPTables. It will also allow you to start
and stop i2p as well. That means you can browse anonymously in Kali
Linux with Anonsurf running in the background. Anonsurf will run and
keep changing IP address every so often or you can simply restart the
process to make it grab a new IP address and thus spoofing your own IP
address. Sounds good?
Und3rf10w forked ParrotSec’s git and made a version for Kali Linux which is very easy and straight forward to install. His repo contains the sources of both the anonsurf and pandora packages from ParrotSec combined into one. Und3rf10w also made some small modifications to the DNS servers to use of Private Internet Access (instead of using FrozenDNS) and added some fixes for users who don’t use the resolvconf application. He also removed some functionality such as the GUI and IceWeasel/Firefox in RAM. There’s a installer script which makes it really easy to install it. You can review the installer script to find out more. This forked version should now work with any Debian or Ubuntu system, but this has only been tested to work on a kali-rolling amd64 system. I am also using the same system but users are advised to test and verify it in their own distro. If it works, then you will be able to hide your IP and gain anonymity as long you’re not signed into any website such as Google, Yahoo etc. I wrote a nice long article comparing different methods i.e. TOR vs VPN vs Proxy on top of each other.
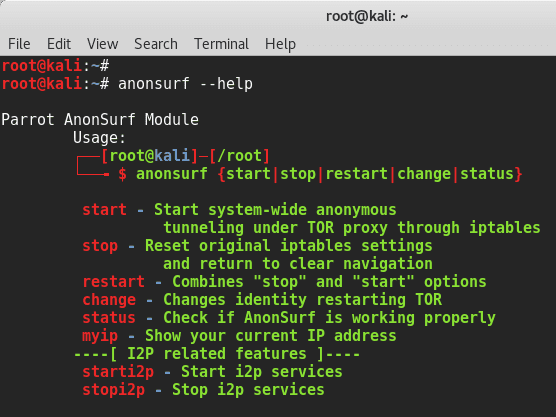
NOTE: This will clear the entire system cache, including active SSH
tunnels or sessions so perhaps not a good idea to run it while working.
It makes the system freeze for sometime (I tried it in a VM).
So here’s how to configure Anonsurf in Kali Linux:
Once it’s downloaded, change directory to kali-anonsurf
In Kali Linux, it will automagically update
The not so obvious thing people doesn’t check is if they are leaking DNS. I usually do it from http://dnsleak.com/ as shown on my post from setting up VPN. However, I did not get any results back, so I used https://www.perfect-privacy.com/dns-leaktest/ and https://torguard.net/vpn-dns-leak-test.php and they seems to think I am in Netherlands or Belgium … so all good.
You can also check if you’re leaking IPv6 in here: http://ipv6leak.com/
Finally I would like to thank ParrotSec and Und3rf10w for taking their time and doing it. I am sure many users around the world would like to use it, specially when your country doesn’t allow access to certain Internet resources.
In case ip spoofing in Kali Linux is a requirement for you, try torsocks. It uses SOCKS proxy which is not commonly used, so chances are you will have fast browsing experiences compared to standard TOR settings.
I think I covered most of anonsurf and browsing anonymously part well. Did I make any mistakes? Do you have a suggestion? Let me know. Comments section is open as always and doesn’t require registration or any validation… so do help others and contribute where applicable.

IP spoofing, also known as IP address forgery or a host file hijack, is a hijacking technique in which a cracker masquerades as a trusted host to conceal his identity, spoof a Web site, hijack browsers, or gain access to a network. We use various methods to spoof our IP addresses, most common being using Proxy, VPN and TOR.
 I
found this interesting tool named Anonsurf and it will anonymize the
entire system under TOR using IPTables. It will also allow you to start
and stop i2p as well. That means you can browse anonymously in Kali
Linux with Anonsurf running in the background. Anonsurf will run and
keep changing IP address every so often or you can simply restart the
process to make it grab a new IP address and thus spoofing your own IP
address. Sounds good?
I
found this interesting tool named Anonsurf and it will anonymize the
entire system under TOR using IPTables. It will also allow you to start
and stop i2p as well. That means you can browse anonymously in Kali
Linux with Anonsurf running in the background. Anonsurf will run and
keep changing IP address every so often or you can simply restart the
process to make it grab a new IP address and thus spoofing your own IP
address. Sounds good?Und3rf10w forked ParrotSec’s git and made a version for Kali Linux which is very easy and straight forward to install. His repo contains the sources of both the anonsurf and pandora packages from ParrotSec combined into one. Und3rf10w also made some small modifications to the DNS servers to use of Private Internet Access (instead of using FrozenDNS) and added some fixes for users who don’t use the resolvconf application. He also removed some functionality such as the GUI and IceWeasel/Firefox in RAM. There’s a installer script which makes it really easy to install it. You can review the installer script to find out more. This forked version should now work with any Debian or Ubuntu system, but this has only been tested to work on a kali-rolling amd64 system. I am also using the same system but users are advised to test and verify it in their own distro. If it works, then you will be able to hide your IP and gain anonymity as long you’re not signed into any website such as Google, Yahoo etc. I wrote a nice long article comparing different methods i.e. TOR vs VPN vs Proxy on top of each other.
anonsurf
Anonsurf will anonymize the entire system under TOR using IPTables. It will also allow you to start and stop i2p as well.NOTE: DO NOT run this asservice anonsurf $COMMAND. Run this asanonsurf $COMMAND

Pandora
Pandora automatically overwrites the RAM when the system is shutting down. Pandora can also be ran manually:pandora bomb
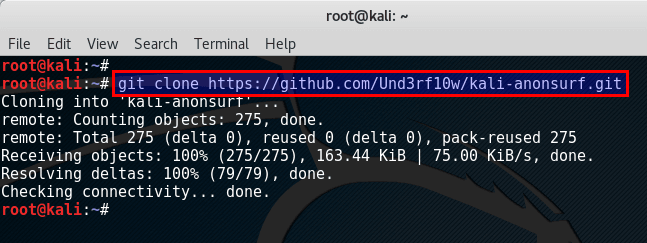
Download Anonsurf
Clone anonsurf from GITroot@kali:~# git clone https://github.com/Und3rf10w/kali-anonsurf.git Cloning into 'kali-anonsurf'... remote: Counting objects: 275, done. remote: Total 275 (delta 0), reused 0 (delta 0), pack-reused 275 Receiving objects: 100% (275/275), 163.44 KiB | 75.00 KiB/s, done. Resolving deltas: 100% (79/79), done. Checking connectivity... done. root@kali:~#

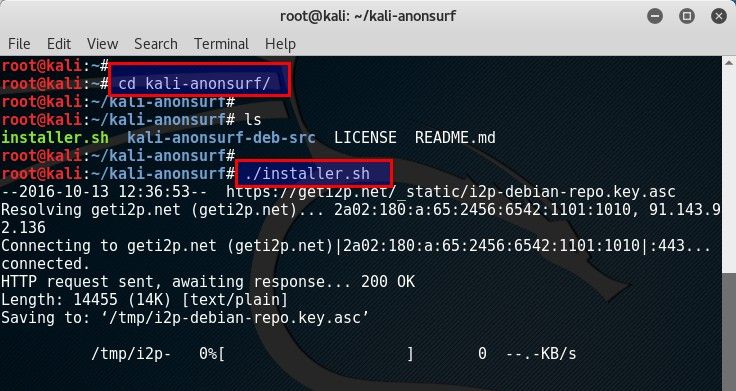
Once it’s downloaded, change directory to kali-anonsurf
root@kali:~# root@kali:~# cd kali-anonsurf/ root@kali:~/kali-anonsurf# root@kali:~/kali-anonsurf# ls installer.sh kali-anonsurf-deb-src LICENSE README.md root@kali:~/kali-anonsurf#
Install anonsurf
With the installer script, it’s very straight forward to install anonsurf in Kali Linux.root@kali:~/kali-anonsurf# ./installer.sh --2016-10-13 12:36:53-- https://geti2p.net/_static/i2p-debian-repo.key.asc Resolving geti2p.net (geti2p.net)... 2a02:180:a:65:2456:6542:1101:1010, 91.143.92.136 Connecting to geti2p.net (geti2p.net)|2a02:180:a:65:2456:6542:1101:1010|:443... connected. HTTP request sent, awaiting response... 200 OK Length: 14455 (14K) [text/plain] Saving to: ‘/tmp/i2p-debian-repo.key.asc’ /tmp/i2p-debian-rep 100%[===================>] 14.12K 21.6KB/s in 0.7s <--------output-----truncated------->

In Kali Linux, it will automagically update
/etc/tor/torrc file and add the following lines:VirtualAddrNetwork 10.192.0.0/10 AutomapHostsOnResolve 1 TransPort 9040 SocksPort 9050 DNSPort 53 RunAsDaemon 1It also changes your resolver configuration to the following:
root@kali:~# cat /etc/resolv.conf nameserver 127.0.0.1 nameserver 209.222.18.222 nameserver 209.222.18.218If you don’t like using Private Internet Access DNS, simply the change DNS in the following lines in
/etc/init.d/anonsurf scriptecho -e 'nameserver 127.0.0.1\nnameserver 209.222.18.222\nnameserver 209.222.18.218' > /etc/resolv.conf echo -e " $GREEN*$BLUE Modified resolv.conf to use Tor and Private Internet Access DNS"
Start anonsurf
To start anonsurf, and pass all under TOR, simply start anonsurf. It will also start TOR if that already been started:root@kali:~# anonsurf start * killing dangerous applications * cleaning some dangerous cache elements [ i ] Stopping IPv6 services: [ i ] Starting anonymous mode: * Tor is not running! starting it for you * Saved iptables rules * Modified resolv.conf to use Tor and Private Internet Access DNS * All traffic was redirected throught Tor [ i ] You are under AnonSurf tunnel root@kali:~#
Find your new Public IP
You can issue the following command to find out your IP adderssroot@kali:~# anonsurf myip My ip is: 1xx.1xx.2xx.1xx
Restart anonsurf
If you want a new IP address, simply restart anonsurf:oot@kali:~# anonsurf restart * killing dangerous applications * cleaning some dangerous cache elements [ i ] Stopping anonymous mode: * Deleted all iptables rules * Iptables rules restored [ i ] Reenabling IPv6 services: * Anonymous mode stopped * killing dangerous applications * cleaning some dangerous cache elements [ i ] Stopping IPv6 services: [ i ] Starting anonymous mode: * Tor is not running! starting it for you * Saved iptables rules * Modified resolv.conf to use Tor and Private Internet Access DNS * All traffic was redirected throught Tor [ i ] You are under AnonSurf tunnelThen simply check your new IP address using the same myip command:
root@kali:~# anonsurf myip My ip is: 1xx.1xx.6x.6x
Stop anonsurf
To stop anonsurf,root@kali:~# anonsurf stop * killing dangerous applications * cleaning some dangerous cache elements [ i ] Stopping anonymous mode: * Deleted all iptables rules * Iptables rules restored [ i ] Reenabling IPv6 services: * Anonymous mode stopped
Testing anonymity
First of all, your IP address definitely changed, so there’s no worry on that side. I checked my public IP from command line, using Google and WhatismyIP. This seems to be working and I was able to browse and compared to just TOR, I think it was slightly faster and more responsive.If you think it’s working slow, simply restart anonsurf and chances are you will end up in a faster connection.The not so obvious thing people doesn’t check is if they are leaking DNS. I usually do it from http://dnsleak.com/ as shown on my post from setting up VPN. However, I did not get any results back, so I used https://www.perfect-privacy.com/dns-leaktest/ and https://torguard.net/vpn-dns-leak-test.php and they seems to think I am in Netherlands or Belgium … so all good.
You can also check if you’re leaking IPv6 in here: http://ipv6leak.com/
Conclusion
Those who doesn’t know what ParrotSec OS is, it is another Security OS similar to Kali Linux developed by Parrot Security. I would give them a go if I were you.Finally I would like to thank ParrotSec and Und3rf10w for taking their time and doing it. I am sure many users around the world would like to use it, specially when your country doesn’t allow access to certain Internet resources.
In case ip spoofing in Kali Linux is a requirement for you, try torsocks. It uses SOCKS proxy which is not commonly used, so chances are you will have fast browsing experiences compared to standard TOR settings.
I think I covered most of anonsurf and browsing anonymously part well. Did I make any mistakes? Do you have a suggestion? Let me know. Comments section is open as always and doesn’t require registration or any validation… so do help others and contribute where applicable.
RELATED ARTICLES




No comments:
Post a Comment