https://cyberarms.wordpress.com/2015/03/01/pulling-remote-word-documents-from-ram-using-kali-linux
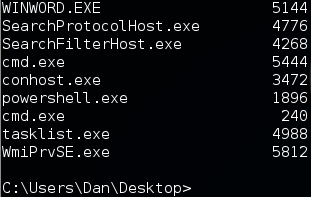
Further down the list we see that the user has an open session of MS Word (WINWORD.EXE):
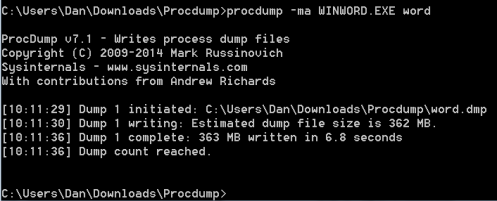
Run the procdump command using the “-ma” switch and the process name “WINWORD.EXE”, lastly we will call the resultant dump file “word” as seen below:
We now have a memory dump stored on our remote system called “word.dmp”. The file is pretty large, 362 MB, we could just download that file back to our Kali system – but we can shrink it. We are really only looking for text in the memory dump. We have two options here, we can use the SysInternals “Strings” program to work through the data dump and remove all the text from it (significantly reducing the download size) or we can download the whole file en-mass back to our Kali system and use the Linux “strings” command to parse it.
The choice is yours, but I will say with just using the default program settings in both, the Linux one did a much better job of parsing the file.
But basically the command is the same in both versions, “strings word.dmp > word.txt”
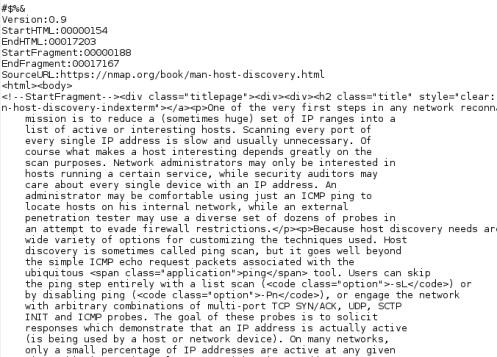
Now if we open the resultant text file in Kali, we see a ton of information – System settings, variables that are set on the system, I even found registry keys mentioned. But eventually we will see this (Produced with the Linux strings command):
Compare that to the Word document we have open on the Windows 7 machine:

Really enjoyed the article on W00tsec about pulling RAW picture images from memory dumps
and thought it would be cool if you could use the same process to pull
information from a remote system’s memory using Kali – and you can!
In this tutorial we will see how to pull a
Word document from a remote machine’s memory, parse it for text and
view it in Kali Linux.
The target system is a Windows 7 PC
running Office 2010. We will start with a remote metasploit meterpreter
shell session already active. So basically we tricked our test system
into running our booby trapped file which created a back door to our
Kali system.
So we want to grab the remote memory, but
we only want the memory in use by the Word process.
Following the
w00tsec tutorial we just need to use the SysInternals ProcDump command.
ProcDump is available from Microsoft’s Technet site, it is part of the SysInternals Suite. This command allows you to pull memory for specific processes.
You may want to grab the SysInternal’s “Strings” program too while you are there. “Strings” is a Windows version of the Linux command that we will be using later.
These programs will need to be uploaded to the target system from Meterpreter.
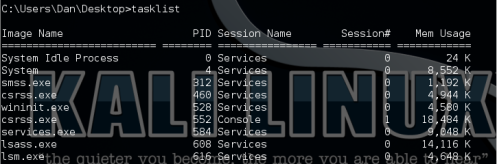
Next, in the Metasploit DOS shell, type “tasklist” to see what is running on the remote Windows system:

Further down the list we see that the user has an open session of MS Word (WINWORD.EXE):

Run the procdump command using the “-ma” switch and the process name “WINWORD.EXE”, lastly we will call the resultant dump file “word” as seen below:

We now have a memory dump stored on our remote system called “word.dmp”. The file is pretty large, 362 MB, we could just download that file back to our Kali system – but we can shrink it. We are really only looking for text in the memory dump. We have two options here, we can use the SysInternals “Strings” program to work through the data dump and remove all the text from it (significantly reducing the download size) or we can download the whole file en-mass back to our Kali system and use the Linux “strings” command to parse it.
The choice is yours, but I will say with just using the default program settings in both, the Linux one did a much better job of parsing the file.
But basically the command is the same in both versions, “strings word.dmp > word.txt”
Now if we open the resultant text file in Kali, we see a ton of information – System settings, variables that are set on the system, I even found registry keys mentioned. But eventually we will see this (Produced with the Linux strings command):

Compare that to the Word document we have open on the Windows 7 machine:

As you can see the Nmap user manual open
on our Windows 7 system has been successfully grabbed from memory
remotely, and we can now view the text on our Kali system!
I know there are other forensics programs
out there that will do basically the same thing, and this is not a
forensically sound way of preserving data needed in a legal case, but it
is a lot of fun doing this manually and opens up some interesting
possibilities!
The best way to defend against these
types of attacks are to follow good security practices against social
engineering and Phishing type attacks. An attacker would need a remote
connection to your system to be able to pull items from your memory. Do
not open unknown or unsolicited attachments in e-mails. Be leery of odd
sounding links sent to you from a friend’s account and use a script
blocker and good AV Internet security program when surfing the web.
Want to learn more about Kali Linux and Metasploit? Check out my book, “Basic Security Testing with Kali Linux“.

No comments:
Post a Comment