https://www.howtoforge.com/tutorial/how-to-setup-file-integrity-monitoring-fim-using-osquery-on-linux-server
Osquery is an open source operating system instrumentation, monitoring, and analytics. Created by Facebook, it exposes an operating system as a high-performance relational database that can be queried using SQL-based queries.
Osquery is a multi-platform software, can be installed on Linux, Windows, MacOS, and FreeBSD. It allows us to explore all of those operating systems' profile, performance, security checking etc, using SQL-based queries.
In this tutorial, we will show you how to setup File Integrity Monitoring (FIM) using osquery. We will be using the Linux operating systems Ubuntu 18.04 and CentOS 7.
Prerequisites
Note:
If you get the error about the yum-config-manager command.
In this step, we will enable the syslog consumption for osquery through the rsyslog.
In this step, we will learn about the osquery configuration components, create the custom osquery configuration, and then deploy the osqueryd as a service.
osquery configuration formatted as a JSON file contains osquery configuration specifications described below.
Note:
In this step, we will configure osquery to monitor important directories such as home, ssh directory, etc, tmp, and the www web root directory using custom FIM packs.
Go to the '/usr/share/osquery/packs' directory and create a new packs configuration file 'fim.conf'.
Now back to the '/etc/osquery' configuration directory and edit the osquery.conf file.
Keep checking the JSON configuration file using the JSON linter 'http://jsonlint.com/' and make sure there is no error.
Go to the '/var/www/' directory and create a new file named 'howtoforge.md'.
For global changes.
The installation and configuration of the File Integrity Monitoring (FIM) on Linux Server Ubuntu and CentOS using osquery has been completed successfully.
Osquery is an open source operating system instrumentation, monitoring, and analytics. Created by Facebook, it exposes an operating system as a high-performance relational database that can be queried using SQL-based queries.
Osquery is a multi-platform software, can be installed on Linux, Windows, MacOS, and FreeBSD. It allows us to explore all of those operating systems' profile, performance, security checking etc, using SQL-based queries.
In this tutorial, we will show you how to setup File Integrity Monitoring (FIM) using osquery. We will be using the Linux operating systems Ubuntu 18.04 and CentOS 7.
Prerequisites
- Linux (Ubuntu or CentOS)
- Root privileges
- Completed first osquery guide
What we will do
- Install osquery on Linux Server
- Enable Syslog Consumption for osquery
- Basic osquery Configuration
- Configure File Integrity Monitoring osquery
- Testing
Step 1 - Install osquery on Linux Server
Osquery provides its own repository for all platform installation, and the first step we are going to do is installing the osquery package FROM the official osquery repository.On Ubuntu
Add the osquery key to the system.
export OSQUERY_KEY=1484120AC4E9F8A1A577AEEE97A80C63C9D8B80B
sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys $OSQUERY_KEY
Add the osquery repository and install the package.sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys $OSQUERY_KEY
sudo add-apt-repository 'deb [arch=amd64] https://pkg.osquery.io/deb deb main'
sudo apt install osquery -y
sudo apt install osquery -y
On CentOS
Add the osquery key to the system.
curl -L https://pkg.osquery.io/rpm/GPG | sudo tee /etc/pki/rpm-gpg/RPM-GPG-KEY-osquery
Add and enable the osquery repository, and install the package.
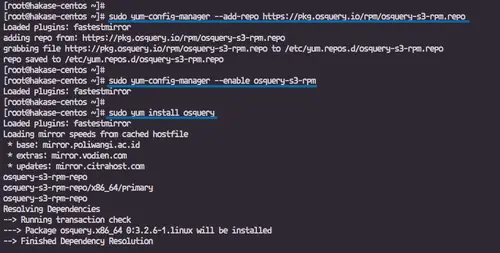
sudo yum-config-manager --add-repo https://pkg.osquery.io/rpm/osquery-s3-rpm.repo
sudo yum-config-manager --enable osquery-s3-rpm
sudo yum install osquery -y
Wait for all packages to be installed.sudo yum-config-manager --enable osquery-s3-rpm
sudo yum install osquery -y
Note:
If you get the error about the yum-config-manager command.
sudo: yum-config-manager: command not found
Install the 'yum-utils' package.
yum -y install yum-utils
Step 2 - Enable Syslog Consumption in osquery
Osquery provides features to read or consume system logs on the Apple MacOS using the Apple System Log (ASL), and for Linux is using the syslog.In this step, we will enable the syslog consumption for osquery through the rsyslog.
On Ubuntu
Install the rsyslog package using the apt command below.
sudo apt install rsyslog -y
On CentOS
Install the rsyslog package using the yum command below.
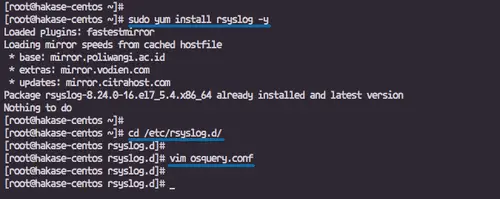
sudo yum install rsyslog -y
After the installation is complete, go to the '/etc/rsyslog.d' directory and create a new configuration file osquery.conf.
cd /etc/rsyslog.d/
vim osquery.conf
Paste the following configuration there.vim osquery.conf
template( name="OsqueryCsvFormat" type="string" string="%timestamp:::date-rfc3339,csv%,%hostname:::csv%,%syslogseverity:::csv%,%syslogfacility-text:::csv%,%syslogtag:::csv%,%msg:::csv%\n" ) *.* action(type="ompipe" Pipe="/var/osquery/syslog_pipe" template="OsqueryCsvFormat")Save and exit.
Step 3 - Basic Configuration osquery
osquery default configuration is 'osquery.conf', usually located in the '/etc/osquery' directory. There are samples of the osquery configuration '/usr/share/osquery/osquery.conf' and sample of osquery packs configuration.In this step, we will learn about the osquery configuration components, create the custom osquery configuration, and then deploy the osqueryd as a service.
osquery configuration formatted as a JSON file contains osquery configuration specifications described below.
- Options: part of the osqueryd CLI command and it determines the apps start and initialization.
- Schedule: Define flow of the scheduled query names to the query details.
- Decorators: Used to add additional "decorations" to results and snapshot logs.
- Packs: a group of the schedule queries.
- More: File Path, YARA, Prometheus, Views, EC2, Chef Configuration.
cd /etc/osquery/
vim osquery.conf
Paste the following configurations there.vim osquery.conf
{
"options": {
"config_plugin": "filesystem",
"logger_plugin": "filesystem",
"logger_path": "/var/log/osquery",
"disable_logging": "false",
"log_result_events": "true",
"schedule_splay_percent": "10",
"pidfile": "/var/osquery/osquery.pidfile",
"events_expiry": "3600",
"database_path": "/var/osquery/osquery.db",
"verbose": "false",
"worker_threads": "2",
"enable_monitor": "true",
"disable_events": "false",
"disable_audit": "false",
"audit_allow_config": "true",
"host_identifier": "hakase-labs",
"enable_syslog": "true",
"syslog_pipe_path": "/var/osquery/syslog_pipe",
"force": "true",
"audit_allow_sockets": "true",
"schedule_default_interval": "3600"
},
"schedule": {
"crontab": {
"query": "SELECT * FROM crontab;",
"interval": 300
},
"system_info": {
"query": "SELECT hostname, cpu_brand, physical_memory FROM system_info;",
"interval": 3600
},
"ssh_login": {
"query": "SELECT username, time, host FROM last WHERE type=7",
"interval": 360
}
},
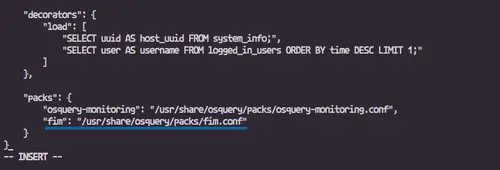
"decorators": {
"load": [
"SELECT uuid AS host_uuid FROM system_info;",
"SELECT user AS username FROM logged_in_users ORDER BY time DESC LIMIT 1;"
]
},
"packs": {
"osquery-monitoring": "/usr/share/osquery/packs/osquery-monitoring.conf"
}
}
Save and exit.Note:
- We're using the 'filesystem' as a config and logger plugins.
- Define the logger path to the '/var/log/osquery' directory.
- Enable the syslog pip to the '/var/syslog/syslog_pipe' file.
- On the scheduler, we define three queries for checking the crontab, system info, and ssh login.
- Enable the osquery packs named 'osquery-monitoring', and packs files located at the '/usr/share/osquery/packs' directory.
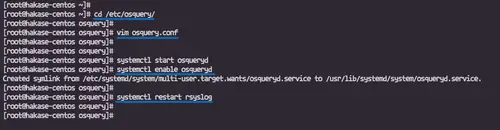
systemctl start osqueryd
systemctl enable osqueryd
And restart the rsyslog service.systemctl enable osqueryd
systemctl restart rsyslog
Basic configuration osquery has been completed.Step 4 - Configure File Integrity Monitoring (FIM) Using osquery
Osquery provides File Integrity Monitoring on Linux and MacOS Darwin using the inotify and FSEvents. Simply, it monitors and detects any changes of files on the defined directory using the 'file_path'and then store all activity to the file_events table.In this step, we will configure osquery to monitor important directories such as home, ssh directory, etc, tmp, and the www web root directory using custom FIM packs.
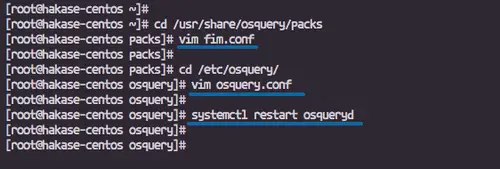
Go to the '/usr/share/osquery/packs' directory and create a new packs configuration file 'fim.conf'.
cd /usr/share/osquery/packs
vim fim.conf
Paste configurations below.vim fim.conf
{
"queries": {
"file_events": {
"query": "SELECT * FROM file_events;",
"removed": false,
"interval": 300
}
},
"file_paths": {
"homes": [
"/root/.ssh/%%",
"/home/%/.ssh/%%"
],
"etc": [
"/etc/%%"
],
"home": [
"/home/%%"
],
"tmp": [
"/tmp/%%"
],
"www": [
"/var/www/%%"
]
}
}
Save and exit.Now back to the '/etc/osquery' configuration directory and edit the osquery.conf file.
cd /etc/osquery/
vim osquery.conf
Add the File Integrity Monitoring packs configuration inside the 'packs' section.vim osquery.conf
"packs": {
"osquery-monitoring": "/usr/share/osquery/packs/osquery-monitoring.conf",
"fim": "/usr/share/osquery/packs/fim.conf"
}
Save and exit, then restart the osqueryd service.
systemctl restart osqueryd
Note:Keep checking the JSON configuration file using the JSON linter 'http://jsonlint.com/' and make sure there is no error.
Step 5 - Testing
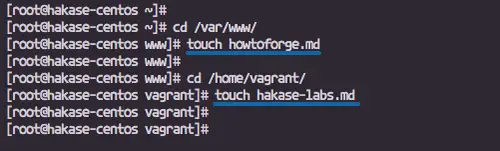
We will test the File Integrity Monitoring packs by creating a new file on the defined directory 'home' and 'www'.Go to the '/var/www/' directory and create a new file named 'howtoforge.md'.
cd /var/www/
touch howtoforge.md
Go to the '/home/youruser/' directory and create a new file named 'hakase-labs.md'.touch howtoforge.md
cd /home/vagrant/
touch hakase-labs.md
Now we will check all logs monitoring using the real-time interactive mode osqueryi and the logs of the osquery results.touch hakase-labs.md
osqueryi
Run the osqueryi command below.
osqueryi --config-path /etc/osquery/osquery.conf
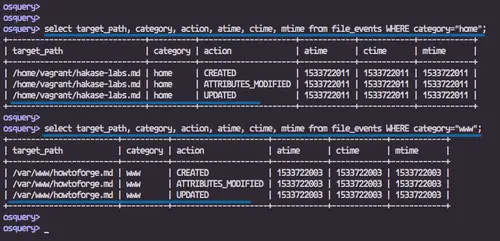
Now check all logs about file changes in the 'file_events' table.For global changes.
select * from file_events;
For 'home' directory.
select target_path, category, action, atime, ctime, mtime from file_events WHERE category="home";
For the 'www' web root directory.
select target_path, category, action, atime, ctime, mtime from file_events WHERE category="www";
osqueryd results log
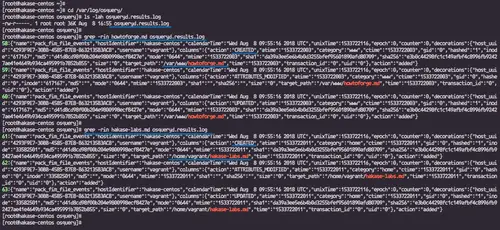
Go to the '/var/log/osquery' directory and you will get the 'osqueryd.results.log' file.
cd /var/log/osquery/
ls -lah osqueryd.results.log
Filter the osquery logs using the 'grep' command.ls -lah osqueryd.results.log
grep -rin howtoforge.md osqueryd.results.log
grep -rin hakase-labs.md osqueryd.results.log
You will see info about those file has been created.grep -rin hakase-labs.md osqueryd.results.log
The installation and configuration of the File Integrity Monitoring (FIM) on Linux Server Ubuntu and CentOS using osquery has been completed successfully.

No comments:
Post a Comment