https://linuxconfig.org/setup-secure-proftpd-server-on-centos-7-with-tls
Lastly, we add an optional anonymous configuration to allow anonymous user to login to FTP server without username and password.
To confirm an opened incoming port
At
this stage any existing system user is able to FTP login to the newly
configured ProFTPD server. Optionally we can create a new user e.g.
Given that our ProFTPD server can be resolved via
Objective
The objective is to first configure a basic ProFTPD server on CentOS 7. Once we have a basic FTP server setup, we will then add FTP passive mode and increase security by adding Transport Layer Security ( TLS ).Lastly, we add an optional anonymous configuration to allow anonymous user to login to FTP server without username and password.
Operating System and Software Versions
- Operating System: - CentOS Linux release 7.5.1804
- Software: - ProFTPD Version 1.3.5e
Requirements
Privileged access to your Ubuntu System as root or viasudo command is required. Difficulty
MEDIUMConventions
- # - requires given linux commands to be executed with root privileges either directly as a root user or by use of
sudocommand - $ - given linux commands to be executed as a regular non-privileged user
Instructions
Basic FTP Configuration
Let's start by the basic installation and configuration of the ProFTP server. This includes, installation, firewall rules definition and client testing.Server Setup
The ProFTPD FTP server is part of a EPEL repository. Therefore, the first step is to enable the EPEL repository and then install the ProFTPD server:# yum install epel-release # yum install proftpdNext, start the ProFTPD server and confirm its correct start by checking for an opened port
21 # service proftpd start # ss -nltNext, we need to puch a whole into server's firewall to allow incoming traffic on port
21 # firewall-cmd --add-port=21/tcp --permanent # firewall-cmd --reload
21 execute: # firewall-cmd --list-ports
lubos with an access to directory /var/ftp-share: # useradd lubos -s /sbin/nologin -d /var/ftp-share # passwd lubos # chmod -R 750 /var/ftp-share # setsebool -P allow_ftpd_full_access=1
Client Connection
At this point we should be able to perform a FTP connection from a remote client computer. The easiest test is to use theftp command.Given that our ProFTPD server can be resolved via
ftp.linuxconfig.org hostname and user lubos is existent execute: $ ftp ftp.linuxconfig.org Connected to ftp.linuxconfig.org. 220 FTP Server ready. Name (ftp.linuxconfig.org:lubos): lubos 331 Password required for lubos Password: 230 User lubos logged in Remote system type is UNIX. Using binary mode to transfer files. ftp>
NOTE: Please note that
at this point we are only able to make "Active FTP connections" only!
Any attempt to create a "Passive FTP connection" will fail.
Passive mode FTP Configuration
Server Setup
To enable our FTP server to accept also passive FTP connection execute the following commands to enable passive connections on IANA registered ephemeral port range:echo "PassivePorts 49152 65534" >> /etc/proftpd.confRestart the ProFTPD server:
# service proftpd restartOpen firewall for ports in range
49152-65534: # firewall-cmd --add-port=49152-65534/tcp --permanent # firewall-cmd --reloadConfirm that the ports have been opened correctly:
# firewall-cmd --list-ports
FTP client connection
As before we can now test the FTP passive connection by using theftp command. Make sure that this time you use the -p option as shown below: $ ftp -p ftp.linuxconfig.org Connected to ftp.linuxconfig.org. 220 FTP Server ready. Name (ftp.linuxconfig.org:lubos): lubos 331 Password required for lubos Password: 230 User lubos logged in Remote system type is UNIX. Using binary mode to transfer files. ftp> ls 227 Entering Passive Mode (192,168,1,111,209,252). 150 Opening ASCII mode data connection for file list 226 Transfer complete ftp>All is working as expect!
Secure FTP server with TLS
Server Setup
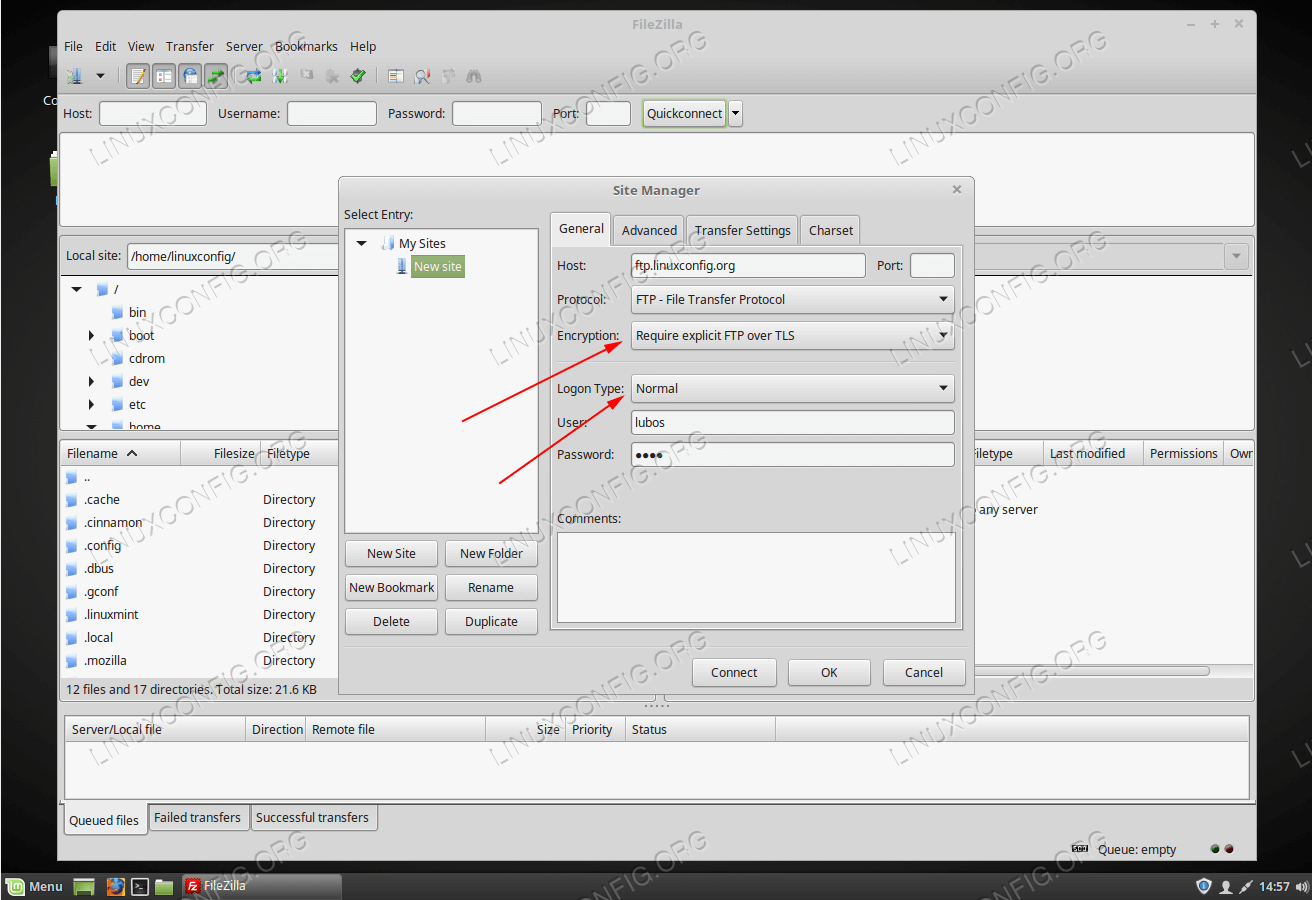
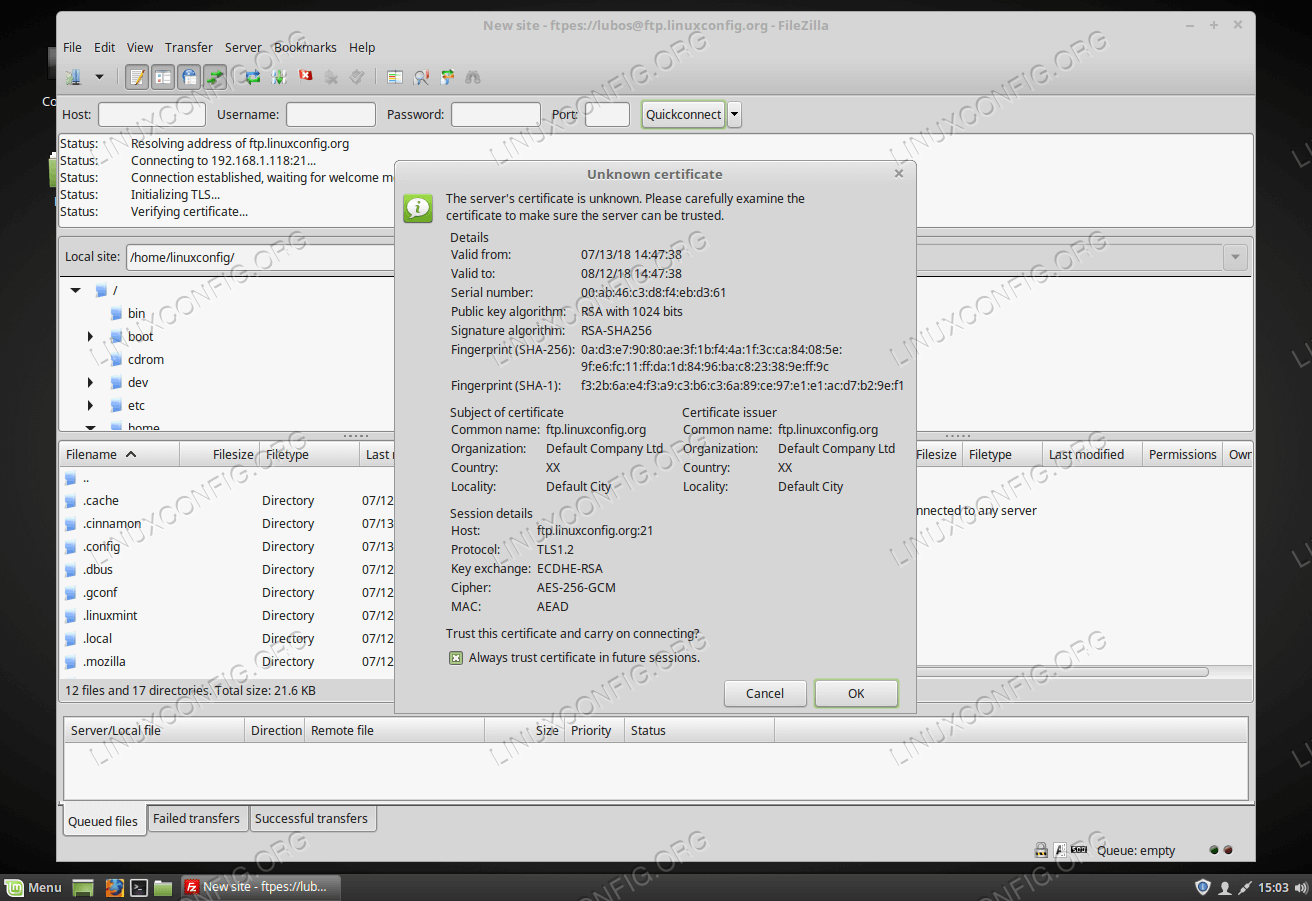
In case you plan to use your FTP server outside of your local area network, it is recommended to use some sort of encryption. Fortunately, configuring ProFTPD with TLS is extremely easy. First, if not available already, install theopenssl package: # yum install opensslNext, create a certificate using the following command. The only required value is
Common Name which is the hostname of your FTP server : # openssl req -x509 -nodes -newkey rsa:1024 -keyout /etc/pki/tls/certs/proftpd.pem -out /etc/pki/tls/certs/proftpd.pem Generating a 1024 bit RSA private key ...++++++ .......++++++ writing new private key to '/etc/pki/tls/certs/proftpd.pem' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]: State or Province Name (full name) []: Locality Name (eg, city) [Default City]: Organization Name (eg, company) [Default Company Ltd]: Organizational Unit Name (eg, section) []: Common Name (eg, your name or your server's hostname) []:ftp.linuxconfig.org Email Address []:Next, as the root user, open
/etc/sysconfig/proftpd using your favorite text editor and change: FROM: PROFTPD_OPTIONS="" TO: PROFTPD_OPTIONS="-DTLS"Once ready, restart the ProFTPD server:
# service proftpd restart
Client connection
This time we use FileZilla as our FTP testing client:Configure anonymous FTP user
Server Setup
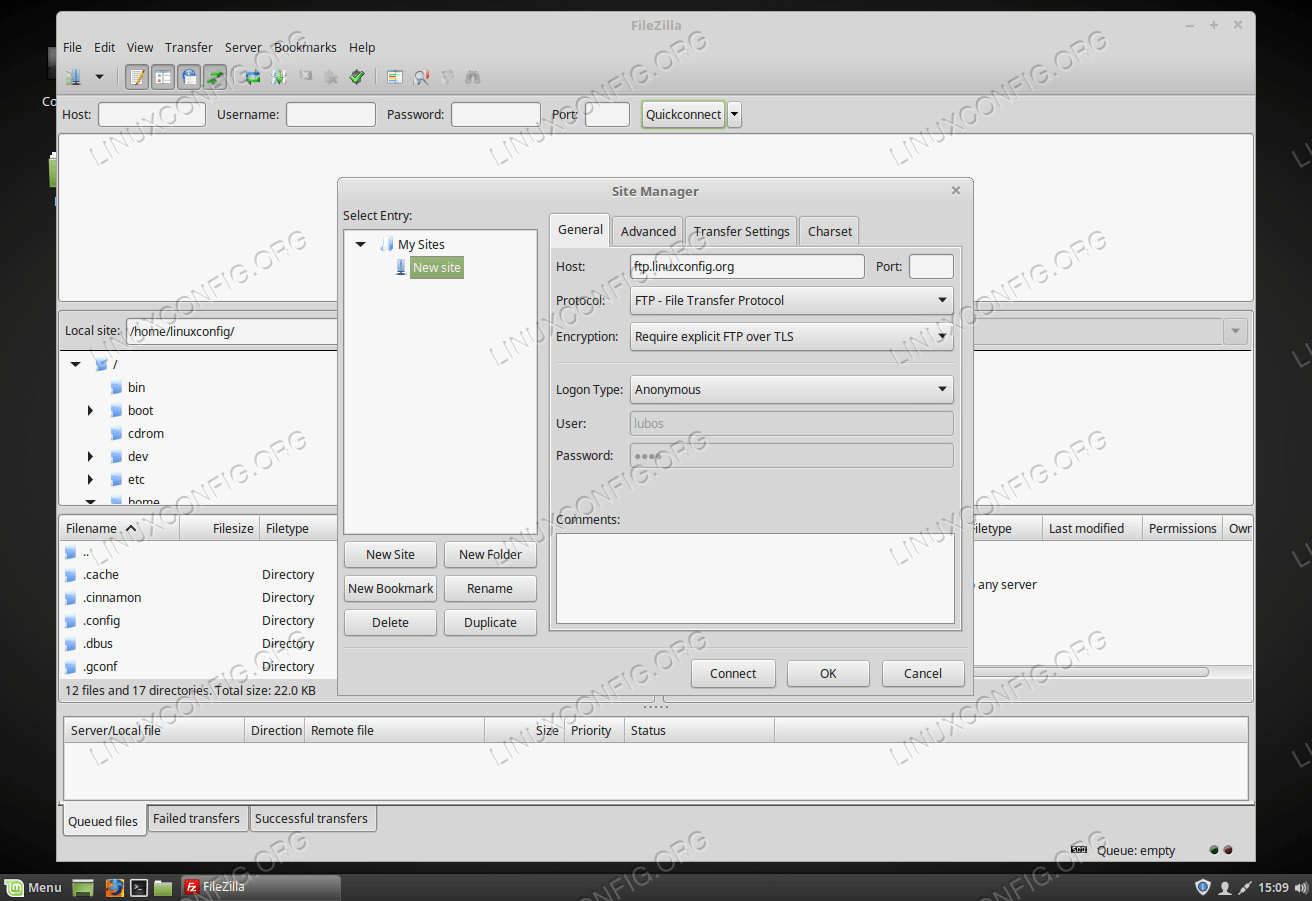
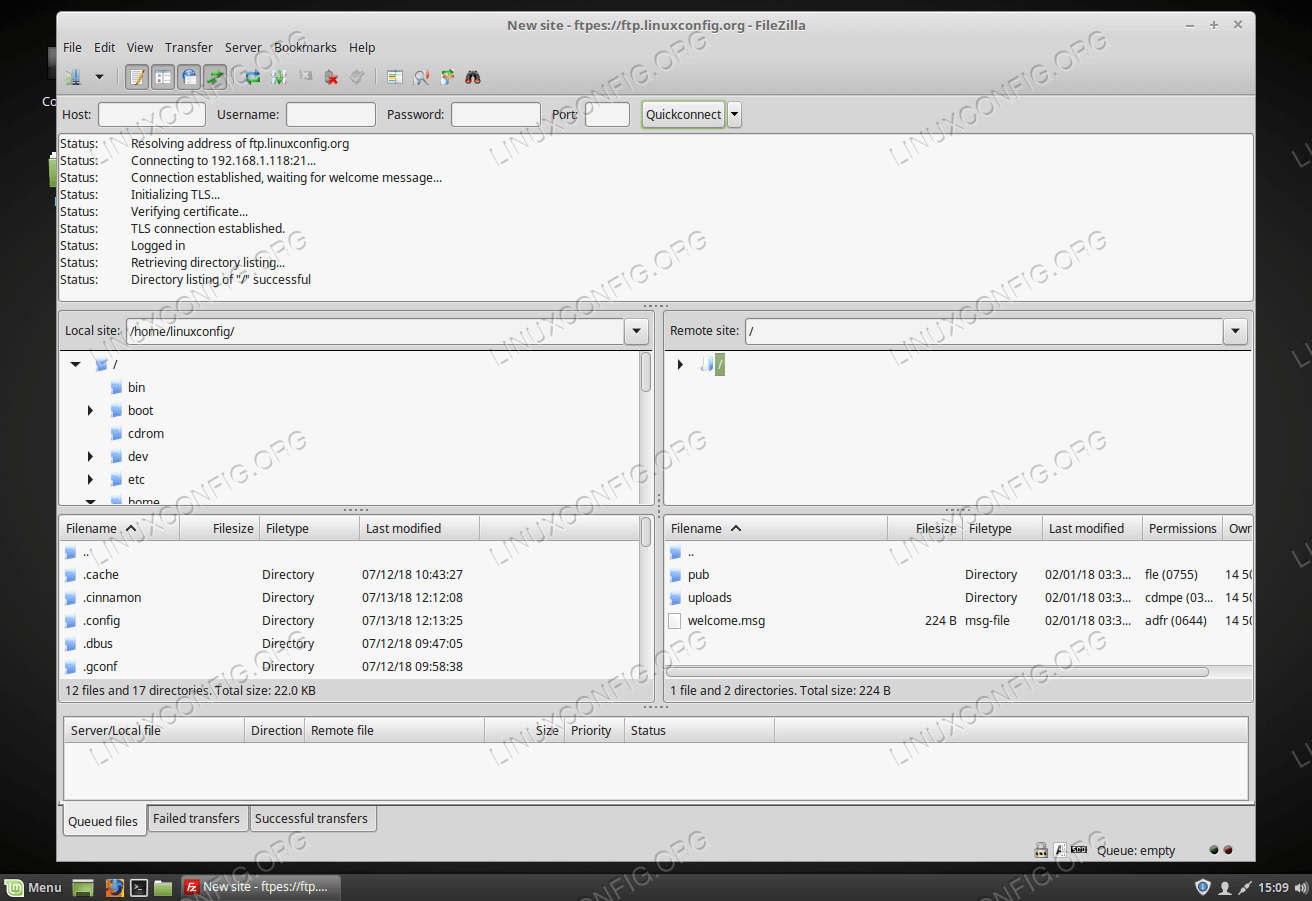
To allow anonymous user to login to the FTP server open/etc/sysconfig/proftpd using your favorite text editor and change: FROM: PROFTPD_OPTIONS="-DTLS" TO: PROFTPD_OPTIONS="-DTLS -DANONYMOUS_FTP"Above we assume that you have alredy enabled TLS previously. When ready restart the FTP server:
# service proftpd restart
Client connection
Using FileZilla as our FTP testing client:Appendix
Block/Refuse User's FTP access
In case you need to block/refuse access to FTP server of any system user add his/her username into/etc/ftpusers. One username per line. Doing so any user attempt to login will fail with 530 login error: $ ftp ftp.linuxconfig.org Connected to ftp.linuxconfig.org. 220 FTP Server ready. Name (ftp.linuxconfig.org:lubos): lubos 331 Password required for lubos Password: 530 Login incorrect. Login failed. Remote system type is UNIX. Using binary mode to transfer files. ftp>




No comments:
Post a Comment