http://linuxtechlab.com/openldap-complete-guide-install-configure-ldap-centos-rhel
OpenLDAP is an open source implementation of LDAP or Lightweight Directory Access Protocol . OpenLDAP allows to store store and organize user related data centrally. OpenLDAP functions like a relational database & can store any data but its normally used as a address book. Its used for authenticating and authorizing of the users. Information stored in OpenLDAP is in hierarchical manner & We can group the users into a single or multiple groups based on necessity.
In this tutorial, we will learn to install & configure LDAP with OpenLDAP, step by step.
(Recommended Read: Beginner’s guide to implementing DNS server using BIND )
[root@ldap ~]# yum install openldap openldap-clients openldap-servers
Once the packages have been installed, we will create password for ldap administrative user with the following command,
[root@ldap ~]# slappasswd
New password:
Re-enter new password:
{SSHA}dMKRmlKAM5YumREa5/TWrd98zwZTBE0c
We will need the encrypted password, so make a note of that. Now start the ldap server & enable it for boot,
$ systemctl start slapd
$ systemctl enable slapd
[root@ldap ~]# cd /etc/openldap/slapd.d/cn=config
[root@ldap ~]# vi olcDatabase={2}hdb.ldif
& edit the following two lines to match your domain,
olcSuffix: dc=linuxtechlab,dc=local
olcRootDN: cn=Manager,dc=linuxtechlab,dc=local
& add the following line to the file.
olcRootPW:{SSHA}dMKRmlKAM5YumREa5/TWrd98zwZTBE0c
here, ‘olcSuffix: dc=linuxtechlab,dc=local’ is used to define the your preferred domain, which in our case in ‘linuxtechlab.local’ & with ‘’olcRootPW’, we have defined the administrator password for Domain admin.
Next make the changes in file ‘/etc/openldap/slapd.d/cn=config/olcDatabase={1}monitor.ldif’ to make it as per domain,
[root@ldap ~]# vi /etc/openldap/slapd.d/cn=config/olcDatabase={1}monitor.ldif
olcAccess: {0}to * by dn.base=”gidNumber=0+uidNumber=0,cn=peercred,cn=extern
al,cn=auth” read by dn.base=”cn=Manager,dc=linuxtechlab,dc=local” read by * none
Save the file & exit. Now run the slaptest to make sure that the configurations made are correct,
[root@localhost ~]# slaptest -u
59fbb825 ldif_read_file: checksum error on “/etc/openldap/slapd.d/cn=config/olcDatabase={1}monitor.ldif”
59fbb825 ldif_read_file: checksum error on “/etc/openldap/slapd.d/cn=config/olcDatabase={2}hdb.ldif”
config file testing succeeded
If you receive any checksum errors, forget about them. Make sure that config testing succeeds.
There is a sample ldap database configuration file located in ‘/usr/share/openldap-servers’, we will use it as reference as our database file. Copy the file to ‘/usr/lib/ldap’ with the following command,
[root@ldap ~]# cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG [root@ldap ~]# chown ldap:ldap /var/lib/ldap/*
Once done, add the following files to the ldap schema,
[root@localhost ~]# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif
[root@localhost ~]# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif
[root@localhost ~]# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif
Next we need to generate a file named ‘base.ldif’ which will contain information regarding our OU,
[root@localhost ~]# vim /root/base.ldif
dn: dc=linuxtechlab,dc=local
dc: linuxtechlab
objectClass: top
objectClass: domain
dn: cn=ldapadm ,dc=linuxtechlab,dc=local
objectClass: organizationalRole
cn: Manager
description: LDAP Manager
dn: ou=Employees,dc=linuxtechlab,dc=local
objectClass: organizationalUnit
ou: Employees
dn: ou=Visitors,dc=linuxtechlab,dc=local
objectClass: organizationalUnit
ou: Visitors
Now build the directory structure with the following command,
[root@localhost ~]# ldapadd -x -W -D “cn=Manager,dc=linuxtechlab,dc=local” -f /root/base.ldif
you will than be asked to enter the root password for LDAP. Upon successful authentication, you should get the following output ,
adding new entry “dc=linuxtechlab,dc=local”
adding new entry “cn=ldapadm ,dc=linuxtechlab,dc=local”
adding new entry “ou=Employees,dc=linuxtechlab,dc=local”
adding new entry “ou=Visitors,dc=linuxtechlab,dc=local”
Our OpenLDAP server is almost complete, we now only have to add some users to our LDAP server. We now will create two users, one named ‘sara’ for our OU named ‘Employees’ & other named ‘Dan’ for OU named ‘Visitors’,
[root@localhost ~]# vi /root/sara.ldif
dn: uid=Sara,ou=Employees,dc=linuxtechlab,dc=local
objectClass: top
objectClass: account
objectClass: posixAccount
objectClass: shadowAccount
cn: sara
uid: sara
uidNumber: 800
gidNumber: 101
homeDirectory: /home/sara
loginShell: /bin/bash
gecos: Sara
userPassword: {crypt}x
shadowLastChange: 17058
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
These are only temporary files & can be deleted after they have been exported to OpenLDAP database or you can keep them as reference to add new users. Next we add the new user in LDAP,
[root@localhost ~]# ldapadd -x -W -D “cn=Manager,dc=linuxtechlab,dc=local” -f /root/sara.ldif
Enter the root LDAP password & you should get the following output upon successful authentication,
adding new entry “cn=Sara Smith,ou=Employees,dc=linuxtechlab,dc=local”
Next we will assign this user ‘sara’ a password with the following command,
[root@localhost ~]# ldappasswd -s Sara@123 -W -D “cn=Manager,dc=linuxtechlab,dc=local” -x “uid=sara,ou=Employees,dc=linuxtechlab,dc=local”
Similarly add the more users. Perform a ldap search after all the users have been added to make sure that all users have been added successfully, use this command,
[root@localhost ~]# ldapsearch -x cn=sara -b dc=linuxtechlab,dc=local
$ yum install -y openldap-clients nss-pam-ldapd
Once the packages have been installed, run the following command to configure the LDAP authentication,
$ authconfig-tui
& configure the ldap authentication as shown in pictures below,


Once done, you can check if the configuration have been successfully or not by using the following command,
$ getent passwd sara
If configurations have been made correctly, you should get the following output,
sara:x:800:101:Sara:/home/sara:/bin/bash
That’s it , we can now use the ldap users to login to the remote machines. With this we end our tutorial on how to install & configure LDAP server on CentOS 7, please feel free to send out your questions using the comment box below.
OpenLDAP is an open source implementation of LDAP or Lightweight Directory Access Protocol . OpenLDAP allows to store store and organize user related data centrally. OpenLDAP functions like a relational database & can store any data but its normally used as a address book. Its used for authenticating and authorizing of the users. Information stored in OpenLDAP is in hierarchical manner & We can group the users into a single or multiple groups based on necessity.
(Recommended Read: Beginner’s guide to implementing DNS server using BIND )
LDAP Installation
All the OpenLDAP packages are available with default package repositories, we need to install ‘openldap’, ‘openldap-clients’ & ‘openldap-servers’ packages. Install them using the following command,[root@ldap ~]# yum install openldap openldap-clients openldap-servers
Once the packages have been installed, we will create password for ldap administrative user with the following command,
[root@ldap ~]# slappasswd
New password:
Re-enter new password:
{SSHA}dMKRmlKAM5YumREa5/TWrd98zwZTBE0c
We will need the encrypted password, so make a note of that. Now start the ldap server & enable it for boot,
$ systemctl start slapd
$ systemctl enable slapd
Configure LDAP
We will configure LDAP server using the configuration file for OpenLDAP, named ‘olcDatabase={2}hdb.ldif’ located at ‘/etc/openldap/slapd.d/cn=config’. Open the file,[root@ldap ~]# cd /etc/openldap/slapd.d/cn=config
[root@ldap ~]# vi olcDatabase={2}hdb.ldif
& edit the following two lines to match your domain,
olcSuffix: dc=linuxtechlab,dc=local
olcRootDN: cn=Manager,dc=linuxtechlab,dc=local
& add the following line to the file.
olcRootPW:{SSHA}dMKRmlKAM5YumREa5/TWrd98zwZTBE0c
here, ‘olcSuffix: dc=linuxtechlab,dc=local’ is used to define the your preferred domain, which in our case in ‘linuxtechlab.local’ & with ‘’olcRootPW’, we have defined the administrator password for Domain admin.
Next make the changes in file ‘/etc/openldap/slapd.d/cn=config/olcDatabase={1}monitor.ldif’ to make it as per domain,
[root@ldap ~]# vi /etc/openldap/slapd.d/cn=config/olcDatabase={1}monitor.ldif
olcAccess: {0}to * by dn.base=”gidNumber=0+uidNumber=0,cn=peercred,cn=extern
al,cn=auth” read by dn.base=”cn=Manager,dc=linuxtechlab,dc=local” read by * none
Save the file & exit. Now run the slaptest to make sure that the configurations made are correct,
[root@localhost ~]# slaptest -u
59fbb825 ldif_read_file: checksum error on “/etc/openldap/slapd.d/cn=config/olcDatabase={1}monitor.ldif”
59fbb825 ldif_read_file: checksum error on “/etc/openldap/slapd.d/cn=config/olcDatabase={2}hdb.ldif”
config file testing succeeded
If you receive any checksum errors, forget about them. Make sure that config testing succeeds.
Setting up LDAP Database
After making the above mentioned configurations, we will now setup a database for OpenLDAP server.There is a sample ldap database configuration file located in ‘/usr/share/openldap-servers’, we will use it as reference as our database file. Copy the file to ‘/usr/lib/ldap’ with the following command,
[root@ldap ~]# cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG [root@ldap ~]# chown ldap:ldap /var/lib/ldap/*
Once done, add the following files to the ldap schema,
[root@localhost ~]# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif
[root@localhost ~]# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif
[root@localhost ~]# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif
Next we need to generate a file named ‘base.ldif’ which will contain information regarding our OU,
[root@localhost ~]# vim /root/base.ldif
dn: dc=linuxtechlab,dc=local
dc: linuxtechlab
objectClass: top
objectClass: domain
dn: cn=ldapadm ,dc=linuxtechlab,dc=local
objectClass: organizationalRole
cn: Manager
description: LDAP Manager
dn: ou=Employees,dc=linuxtechlab,dc=local
objectClass: organizationalUnit
ou: Employees
dn: ou=Visitors,dc=linuxtechlab,dc=local
objectClass: organizationalUnit
ou: Visitors
Now build the directory structure with the following command,
[root@localhost ~]# ldapadd -x -W -D “cn=Manager,dc=linuxtechlab,dc=local” -f /root/base.ldif
you will than be asked to enter the root password for LDAP. Upon successful authentication, you should get the following output ,
adding new entry “dc=linuxtechlab,dc=local”
adding new entry “cn=ldapadm ,dc=linuxtechlab,dc=local”
adding new entry “ou=Employees,dc=linuxtechlab,dc=local”
adding new entry “ou=Visitors,dc=linuxtechlab,dc=local”
Our OpenLDAP server is almost complete, we now only have to add some users to our LDAP server. We now will create two users, one named ‘sara’ for our OU named ‘Employees’ & other named ‘Dan’ for OU named ‘Visitors’,
[root@localhost ~]# vi /root/sara.ldif
dn: uid=Sara,ou=Employees,dc=linuxtechlab,dc=local
objectClass: top
objectClass: account
objectClass: posixAccount
objectClass: shadowAccount
cn: sara
uid: sara
uidNumber: 800
gidNumber: 101
homeDirectory: /home/sara
loginShell: /bin/bash
gecos: Sara
userPassword: {crypt}x
shadowLastChange: 17058
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
These are only temporary files & can be deleted after they have been exported to OpenLDAP database or you can keep them as reference to add new users. Next we add the new user in LDAP,
[root@localhost ~]# ldapadd -x -W -D “cn=Manager,dc=linuxtechlab,dc=local” -f /root/sara.ldif
Enter the root LDAP password & you should get the following output upon successful authentication,
adding new entry “cn=Sara Smith,ou=Employees,dc=linuxtechlab,dc=local”
Next we will assign this user ‘sara’ a password with the following command,
[root@localhost ~]# ldappasswd -s Sara@123 -W -D “cn=Manager,dc=linuxtechlab,dc=local” -x “uid=sara,ou=Employees,dc=linuxtechlab,dc=local”
Similarly add the more users. Perform a ldap search after all the users have been added to make sure that all users have been added successfully, use this command,
[root@localhost ~]# ldapsearch -x cn=sara -b dc=linuxtechlab,dc=local
Adding Ldap authentication to a remote machine
Now that we have our OpenLDAP ready with some users configured, we will add the ldap authentication to a remote machine & will use our LDAP users for logging into the system. Firstly open the terminal on remote machine & install the following packages to install OpneLDAP client on the machine,$ yum install -y openldap-clients nss-pam-ldapd
Once the packages have been installed, run the following command to configure the LDAP authentication,
$ authconfig-tui
& configure the ldap authentication as shown in pictures below,
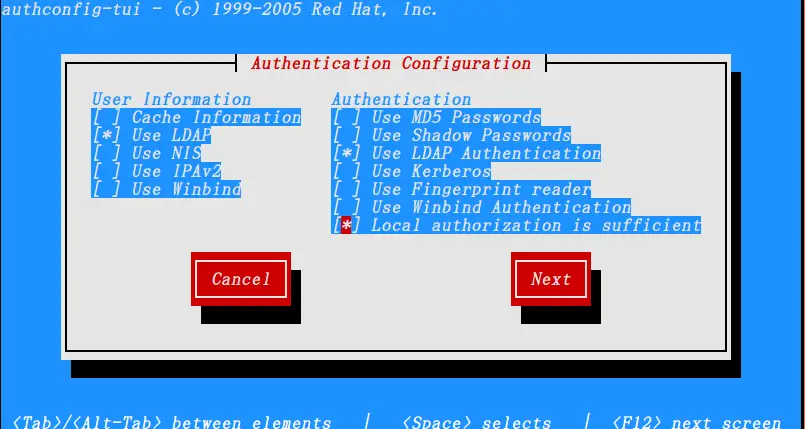
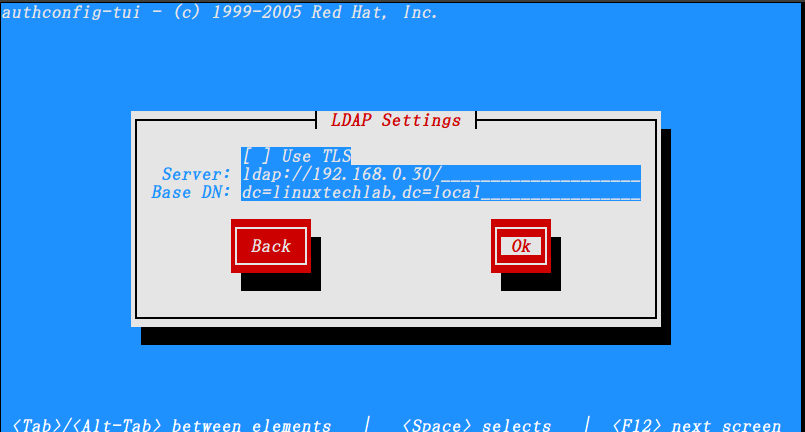
Once done, you can check if the configuration have been successfully or not by using the following command,
$ getent passwd sara
If configurations have been made correctly, you should get the following output,
sara:x:800:101:Sara:/home/sara:/bin/bash
That’s it , we can now use the ldap users to login to the remote machines. With this we end our tutorial on how to install & configure LDAP server on CentOS 7, please feel free to send out your questions using the comment box below.

No comments:
Post a Comment