https://www.howtoforge.com/tutorial/how-to-configure-pureftpd-to-accept-tls-sessions-on-centos-7
This article explains how to configure PureFTPd to accept TLS sessions on a CentOS 7 server. Plain FTP is an insecure protocol because all passwords and all data are transferred in clear text. By using TLS, the whole communication can be encrypted, thus making FTP much more secure.
State or Province Name (full name) []:<-- enter="" name.="" or="" province="" span="" state="" your="">
Locality Name (eg, city) [Default City]:<-- city.="" enter="" span="" your="">
Organization Name (eg, company) [Default Company Ltd]:<-- company="" e.g.="" enter="" name="" of="" organization="" span="" the="" your="">
Organizational Unit Name (eg, section) []:<-- department="" e.g.="" enter="" name="" organizational="" span="" unit="" your="">
Common Name (eg, your name or your server's hostname) []:<-- domain="" e.g.="" enter="" fully="" name="" of="" qualified="" server1.example.com="" span="" system="" the="">
Email Address []:<-- address.="" email="" enter="" span="" your="">
Change the permissions of the SSL certificate:
In FileZilla, open the Site Manager:
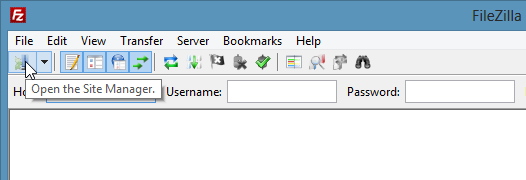
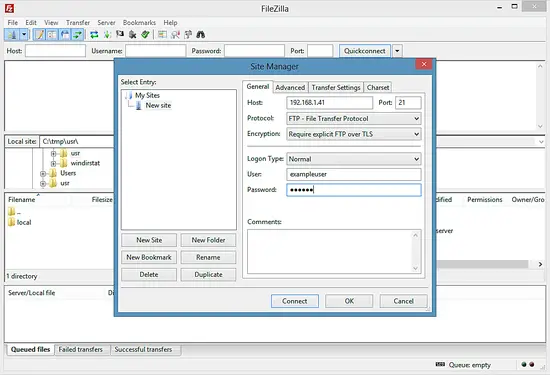
Select the server that uses PureFTPd with TLS; in the Server Type drop-down menu, select Require Explicit FTP over TLS instead of normal FTP:
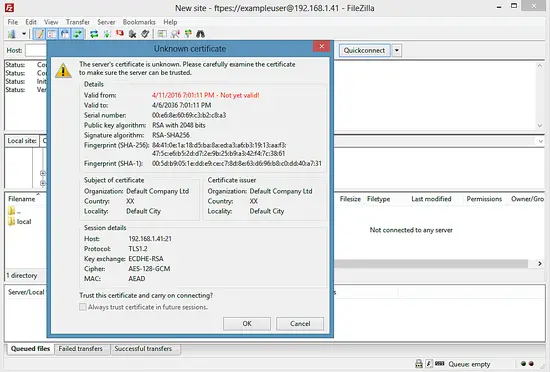
Now you can connect to the server. If you do this for the first time, you must accept the server's new SSL certificate:
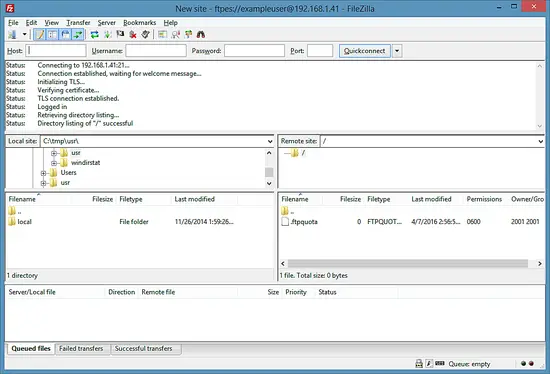
If everything goes well, you should now be logged in on the server:
This article explains how to configure PureFTPd to accept TLS sessions on a CentOS 7 server. Plain FTP is an insecure protocol because all passwords and all data are transferred in clear text. By using TLS, the whole communication can be encrypted, thus making FTP much more secure.
1 Preliminary Note
You should have a working PureFTPd setup on your CentOS 7 server, e.g. as shown in this tutorial: Virtual Hosting With PureFTPd And MySQL (Incl. Quota And Bandwidth Management) On CentOS 7.2 Installing OpenSSL
OpenSSL is needed by TLS; to install OpenSSL, we simply run:
yum install openssl
3 Configuring PureFTPd
Open /etc/pure-ftpd/pure-ftpd.conf...
nano /etc/pure-ftpd/pure-ftpd.conf
If you want to allow FTP and TLS sessions, set TLS to 1:[...] # This option can accept three values : # 0 : disable SSL/TLS encryption layer (default). # 1 : accept both traditional and encrypted sessions. # 2 : refuse connections that don't use SSL/TLS security mechanisms, # including anonymous sessions. # Do _not_ uncomment this blindly. Be sure that : # 1) Your server has been compiled with SSL/TLS support (--with-tls), # 2) A valid certificate is in place, # 3) Only compatible clients will log in. TLS 1 [...]If you want to accept TLS sessions only (no FTP), set TLS to 2:
[...] # This option can accept three values : # 0 : disable SSL/TLS encryption layer (default). # 1 : accept both traditional and encrypted sessions. # 2 : refuse connections that don't use SSL/TLS security mechanisms, # including anonymous sessions. # Do _not_ uncomment this blindly. Be sure that : # 1) Your server has been compiled with SSL/TLS support (--with-tls), # 2) A valid certificate is in place, # 3) Only compatible clients will log in. TLS 2 [...]To not allow TLS at all (only FTP), set TLS to 0:
[...] # This option can accept three values : # 0 : disable SSL/TLS encryption layer (default). # 1 : accept both traditional and encrypted sessions. # 2 : refuse connections that don't use SSL/TLS security mechanisms, # including anonymous sessions. # Do _not_ uncomment this blindly. Be sure that : # 1) Your server has been compiled with SSL/TLS support (--with-tls), # 2) A valid certificate is in place, # 3) Only compatible clients will log in. TLS 0 [...]Then remove the # in front of the following 2 lines:
TLSCipherSuite HIGH CertFile /etc/ssl/private/pure-ftpd.pemand save the altered configuration file.
4 Creating The SSL Certificate For TLS
In order to use TLS, we must create an SSL certificate. I create it in /etc/ssl/private/, therefore I create that directory first:
mkdir -p /etc/ssl/private/
Afterwards, we can generate the SSL certificate as follows:
openssl req -x509 -nodes -days 7300 -newkey rsa:2048 -keyout /etc/ssl/private/pure-ftpd.pem -out /etc/ssl/private/pure-ftpd.pem
Country Name (2 letter code) [XX]: <-- country="" e.g.="" enter="" name="" span="" your="">State or Province Name (full name) []:<-- enter="" name.="" or="" province="" span="" state="" your="">
Locality Name (eg, city) [Default City]:<-- city.="" enter="" span="" your="">
Organization Name (eg, company) [Default Company Ltd]:<-- company="" e.g.="" enter="" name="" of="" organization="" span="" the="" your="">
Organizational Unit Name (eg, section) []:<-- department="" e.g.="" enter="" name="" organizational="" span="" unit="" your="">
Common Name (eg, your name or your server's hostname) []:<-- domain="" e.g.="" enter="" fully="" name="" of="" qualified="" server1.example.com="" span="" system="" the="">
Email Address []:<-- address.="" email="" enter="" span="" your="">
chmod 600 /etc/ssl/private/pure-ftpd.pem
Finally, restart PureFTPd:
systemctl restart pure-ftpd.service
That's it. You can now try to connect using your FTP client; however, you should configure your FTP client to use TLS - see the next chapter how to do this with FileZilla.5 Configuring FileZilla For TLS
In order to use FTP with TLS, you need an FTP client that supports TLS, such as FileZilla or the FireFTP plugin in Firefox.In FileZilla, open the Site Manager:

Select the server that uses PureFTPd with TLS; in the Server Type drop-down menu, select Require Explicit FTP over TLS instead of normal FTP:

Now you can connect to the server. If you do this for the first time, you must accept the server's new SSL certificate:

If everything goes well, you should now be logged in on the server:

6 Links
- PureFTPd: http://www.pureftpd.org/
- FileZilla: http://filezilla-project.org/
- CentOS: http://www.centos.org/

No comments:
Post a Comment