Maybe you want to liberate your iPhone from Apple's clutches. Maybe you just want to tinker with something new.
Still a Work in Progress
Graphic: Eliza WeeAlthough this port does everything that you expect your smartphone to be able to do, it isn't usable for day-to-day activities just yet--I haven't implemented any power-management functions, so a fully charged iPhone running Android will last only an hour or so.
A few bugs and performance issues remain, too, so while the phone will be usable, it won't be fast. If you do something unexpected (such as forcing the iPhone off), there is a small chance that you may end up restoring your device.
However, it is impossible for any bugs to brick or disable your iPhone permanently.
Finally, media syncing is not working, so loading your media onto your phone is kind of a pain. I'm working as hard as I can, though, and I expect to fix these issues soon.
Required Reading
Start by brushing up on the fundamentals of iPhone maintenance: how to get your iPhone into
Recovery Mode, how to put it into
DFU Mode, and how to perform a firmware restore from those modes.
The iPhone is a well-engineered device, and it is virtually impossible to brick if you know these techniques. If all else fails, remember that you can always restore using DFU Mode.
You'll also need to be reasonably comfortable working in a command-line interface, and unless you're confident in trying to compile your own binaries, you'll need a PC running Linux (or a Linux virtual machine).
What You Need
1. A first-generation iPhone or an
iPhone 3G with firmware versions between 2.0 and 3.1.2, jailbroken with
Redsn0w,
Blacksn0w, or
PwnageTool.
If you already updated your handset to 3.1.3 or to a 4.0 beta, you must use PwnageTool to create a jailbroken 3.1.2 .ipsw file to restore down to.
Note that I am explicitly excluding the
iPhone 3GS, all
iPod Touch models, and the
iPad. This hack will not work with those devices (yet). I am also explicitly excluding iPhone OS 3.1.3 and all of the 4.0 betas. It will not work with the
Spirit jailbreak, either.
If you haven't yet jailbroken your iPhone, don't worry--it's a simple process that consists mainly of pressing buttons on the device when prompted and clicking the next button in a wizard.
I humbly recommend
Redsn0w, since I wrote much of the code for that program.
2. A 32-bit Linux system or virtual machine (I recommend
Ubuntu). See "
How to Easily Install Ubuntu Linux on Any PC" for instructions if you don't already have Ubuntu.
Although much of the process can be conducted on any machine, one of the tools involved (called 'oibc') has not yet been ported to Windows.
In addition, the binaries I provide are compiled on a 32-bit Ubuntu machine.
All of the utilities compile for Linux and Mac, however, so if you're feeling adventurous, compile the sources at
github.com/planetbeing/iphonelinux and
github.com/planetbeing/xpwn instead of using the binaries.
3. The prebuilt images and binaries; the exact files you use depend on whether you have a
first-generation iPhone or an
iPhone 3G.
4. The iPhone OS 3.1.2 .ipsw file for your device, namely either iPhone1,1_3.1.2_7D11_Restore.ipsw or iPhone1,2_3.1.2_7D11_Restore.ipsw.
Chances are, you already have this file somewhere on your computer, but if you need it, you can
download it.
5. The firmware for the
Marvell WLAN chip inside the iPhone. Go to the URL, and on the right side of the page you should see a drop-down menu labeled 'Choose your platform'.
Select
Linux 2.6 - Fedora from the drop-down menu and click the
Search button underneath. Download the file labeled SD-8686-LINUX26-SYSKT-9.70.3.p24-26409.P45-GPL.
You'll get a file called SD-8686-LINUX26-SYSKT-9.70.3.p24-26409.P45-GPL.zip.
Android on iPhone, Step-by-Step
The first steps collect the multitouch and WLAN firmware for the iPhone.
We cannot legally redistribute these binary blobs, so it is necessary for you to extract them from the .ipsw file and Marvell's Website.
1. On the Linux machine, create a folder named
firmware in your home directory.
2. Extract SD-8686-FEDORA26FC6-SYSKT-GPL-9.70.3.p24-26409.P45.tar from SD-8686-LINUX26-SYSKT-9.70.3.p24-26409.P45-GPL.zip to a temporary folder.
3. Extract FwImage/helper_sd.bin and FwImage/sd8686.bin from SD-8686-FEDORA26FC6-SYSKT-GPL-9.70.3.p24-26409.P45.tar and put them inside your 'firmware' folder.
4. Rename helper_sd.bin to
sd8686_helper.bin.
You have your WLAN firmware at this point. Now for the multitouch firmware.
5. On the Linux machine, create a folder named
idroid in your home directory and extract utils/dripwn from the prebuilt tarball (.tar archive) you downloaded into it.
6. Copy or move the 3.1.2 .ipsw file you obtained from Apple's Website into the same 'idroid' folder as dripwn.
7. Start a command-line shell (Terminal under Ubuntu) and navigate to the 'idroid' folder you created. You can type
cd ~/idroid to do this.
8. Go to
this page if you have an iPhone 3G or
this page if you have an older iPhone. Copy the VFDecrypt key.
9. In the shell you started earlier, if you have a first-generation iPhone, type the following:
./dripwn iPhone1,1_3.1.2_7D11_Restore.ipsw [the VFDecrypt key you copied]
If you have a iPhone 3G, type the following:
./dripwn iPhone1,2_3.1.2_7D11_Restore.ipsw [the VFDecrypt key you copied]
10. After a while, the command will finish and you will have zephyr_main.bin, zephyr_aspeed.bin, and zephyr2.bin in your 'idroid' folder.
Move these files into the 'firmware' folder.
You now have all the files needed for Android, and you can begin installing it.
11. If you haven't already, install the OpenSSH tool on your iPhone via
Cydia.
12. If you just installed OpenSSH, connect to your iPhone via SSH, log in as root with the password
alpine, and type
passwd root to change the password for root.
Then, enter
passwd mobile to change the password for the mobile user.
Don't skip this step. All of the
iPhone worms out there affect you only if you haven't changed the SSH password from the default.
13. Extract prebuilt/android.img.gz, prebuilt/cache.img, prebuilt/ramdisk.img, prebuilt/system.img, prebuilt/userdata.img, and zImage from the prebuilt tarball.
14. Use the 'scp' command or an SFTP client to upload all of these files into the /private/var folder on the iPhone.
You can use these commands on Linux, if you wish to use scp instead of an SFTP graphical-interface client.
Assuming you're in the same folder as the files, enter:
scp android.img.gz root@[ip address of iPhone]:/private/var/
scp cache.img root@[ip address of iPhone]:/private/var/
scp ramdisk.img root@[ip address of iPhone]:/private/var/
scp system.img root@[ip address of iPhone]:/private/var/
scp userdata.img root@[ip address of iPhone]:/private/var/
scp zImage root@[ip address of iPhone]:/private/var/
15. Using the SFTP client or scp, create a folder called
firmware in the /private/var folder on the iPhone; afterward, upload all the files from the 'firmware' folder you created earlier to it.
If the 'firmware' folder you created earlier is inside your home directory, you can use the following command:
scp -r ~/firmware/ root@[ip address of iPhone]:/private/var/firmware
16. Reboot your iPhone. As a safety precaution, check to make sure that the files are still present after the reboot and that they all have the right sizes.
An incorrect file size is one that does not exactly match the source file size (for example, system.img is not 71327744 bytes, android.img.gz is not 2161556 bytes, or zImage is not 2364280 bytes on the 3G or not 2356044 bytes on the older iPhone).
Many people have trouble with this process because not all of the files reached their iPhone in one piece.
17. Extract utils/oibc, utils/loadibec, and prebuilt/openiboot.img3 from the prebuilt tarball into your 'idroid' folder.
18. Shut down the iPhone and place it into Recovery Mode: With the iPhone powered off and plugged into the computer via USB, push Hold and Home simultaneously, and then let go of Hold after the backlight turns on.
Continue holding Home until the 'Connect to iTunes' image appears on the screen.
19. Run the following commands in Terminal (you'll need to install libusb-0.1-4 with Synaptics or 'apt-get' if you haven't already):
cd ~/idroid
sudo ./loadibec openiboot.img3
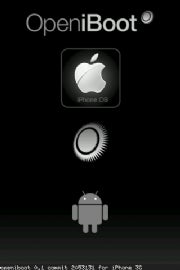
If all goes well, the 'openiboot' boot menu should now appear!
20. Use either the volume-control buttons or the Hold button to select the second menu option, Console. Tap the Home button to launch it.
A text-mode console should start running on your screen, ending with a 'Welcome to openiboot' message.
21. Type sudo ./oibc in Terminal.
The same messages that appeared on the iPhone screen should now appear in Terminal.
You should next make a backup of the NOR (the device on which the iPhone's bootloader is stored) in case something goes wrong, so you don't brick your iPhone.
22. Type nor_read 0x09000000 0x0 1048576 in Terminal/oibc. This will read the entire NOR into main memory.
23. Type ~norbackup.bin@0x09000000:1048576 in Terminal/oibc. A file will appear in the 'idroid' folder called norbackup.bin. Keep this somewhere safe.
The command uploads the NOR to the computer. After you make this backup, you are now free to modify the NOR.
The next step installs OpeniBoot onto the NOR, supplanting the existing Apple iBoot bootloader.
24. Type install in Terminal/oibc.
This process may take a few minutes. Wait until the installation-complete message appears.
25. Type reboot in Terminal/oibc and then exit out of it by pressing Ctrl-C.
The OpeniBoot menu should now come up whenever you boot your iPhone. Note that you can uninstall OpeniBoot from oibc with the 'uninstall' command.
Type help for a list of all OpeniBoot commands.
You can still get into the iPhone OS's recovery mode by holding down Home on the iPhone OS option in the menu until the 'Connect to iTunes' image appears (instead of just tapping Home).
You should be finished! Use the OpeniBoot menu to boot Android by selecting that OS from the menu whenever you wish.
Unfortunately, no good method to shut down Android exists yet, so the only way to turn it off is to hold down the Hold and Home buttons until you've forced the phone off.
Check out iDroidWiki for more tutorials and tips on what you can do with your new Android iPhone.