http://securityaffairs.co/wordpress/8259/security/ddos-attacks-so-simple-so-dangerous.html?goback=%2Egde_1873806_member_178451129
Article Published on DDoS Attacks PT Extra 05_2012
The article proposes an analysis of DDoSattacks, explaining how the offensive technique is used in several contexts to hit strategic targets for different purposes. The discussion is supported with the statistics provided by the principal security firms that provide solutions to protect infrastructures from this kind of attacks. The article also include a specific part on the new factors that could support DDoS attacks such as the introduction of IPv6 protocol and the diffusion of mobile platforms.
Introduction
Let’s introduce one of the most diffused type of cyber attacks that represents a great concern for governments and institutions, the DDoS (Distributed Denial of Service). The attack is conducted with the intent to make a network resources unavailable and usually involve a large number of machines that target the same objective interrupting or suspending the services it provides. The principle on which the attack method is based is the saturation of the resources available to the targets that are flooded by legitimated traffic that are not able to process. The consuming of the resources of final target may usually causes the slowdown in services provided or even complete blockage of the same. It must be clear that Denial-of-service attacks are considered violations of the Internet Architecture Board’s Internet proper use policy, an ethic manifesto for internet use. The IAB is the committee charged with oversight of the technical and engineering development of the Internet by the Internet Society (ISOC). DDoS attacks is commonly considered a cyber crime by governments all around the world, they constitute violations of the laws of individual countries, but despite this global acceptance is still very difficult to be pursued due the different legislation and territorial jurisdictions.
The raise of DDoS attacks
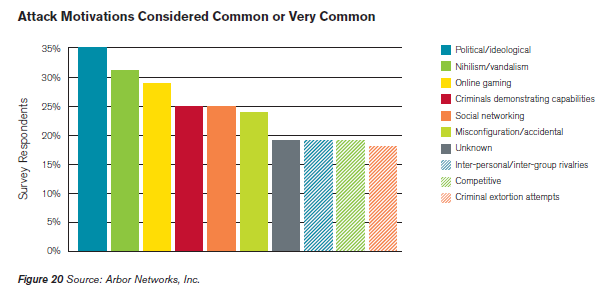
Despite it is relative ease organize a DDoS attack, it still represents one of the most feared offensive forms for its ability to interfere with the services provided, DDoS attacks are so widely used by hackers and hacktivists, but also represent a viable military options in the event of a cyber attack against critical enemy structures. According “Worldwide Infrastructure Security Report” published by Arbor Networks, a leading provider of network security and management solutions, Ideologically-Motivated ‘Hacktivism’ and Vandalism Are the Most Readily-Identified DDoS. Arbor Networks has provided evidence that in 2011 behind the majority of DDoS attacks there were group of hacktivists that have involved critical masses in the manifestation of their dissent, 35% reported political or ideological attack motivation meanwhile 31% reported nihilism or vandalism as attack motivation. Today is possible to retrieve tool for DDoS attacks freely such as the famous “low orbit ion cannon” (LOIC), and it’s equally simple rent a botnet with a few tens of dollars, this factor have transformed the DDoS attacks in one of the most dangerous cyber threat. We are facing with crime industry that is arranging specific services to rent ad hoc network used to amplify attacks, a phenomenon in constant growth. We have also consider that the attacks are becoming daily more sophisticated addressing various level of network stack and often in multilayered offensive.
A great contribution to the raise of number of DDoS attacks is given also by the diffusion of malware agents, it is the case of a newer version of the Russkill bot also also known as Dirt Jumper, responsible for a many attacks. Iit seems that the author of the malware has released another DDoS toolkit that has similar structure and functionalities, named Pandora, that will give a sensible contribute in term of cyber attacks. The increase of the attacks is also motivated by a couple of other factor, the diffusion of mobile devices and also the introduction of IPv6 protocol. One of the IT sector that is interested by the major growth is without doubt the mobile, an increasing number of platforms and related application has been developed in the last mouth consolidating the trend. Of course with growth has been observed a sensible increasing of cyber attacks on the mobile sector, today still vulnerable on the security perspective. To an impressive growth in the demand is not corresponded the awareness of the threat, the user ignores most of the time the potential of its smartphone and threats which it is exposed. Mobile botnet is a botnet that targets mobile devices such as smartphones, attempting to gain complete control of them. Mobile botnets take advantage of unpatched exploits to provide hackers with root permissions over the compromised mobile device, enabling hackers to send e-mail or text messages, make phone calls, spy on users, access contacts and photos, and more. The main problem is that botnets go undetected and this make really difficult to tackle. The malware spread themself sending the agents to other devices via e-mail messages or text messages. But cyber threat related to mobile devices is not also related to a malware infection, due the difficult to track the origin of attacks in many cases these platform are used to launch attacks in deliberate way, it’s the case for example of a user that decide to participate to a DDoS attacks downloading a specific toolto flood with traffic the final target. As anticipated another meaningful phenomenon is the introduction of IPv6 protocol, the switchover from the protocol IPv4, to IPv6 will create vast numbers of new internet addresses that could be used to orange a DDoS attacks. Despite this kind of incidents are relatively rare, the introduction of the new protocol represents an attractive opportunity for cyber criminals that intend to move a DDoS attack, let’s consider that the first attacks based on IPv6 addresses have been already discovered.
DDoS Statistics
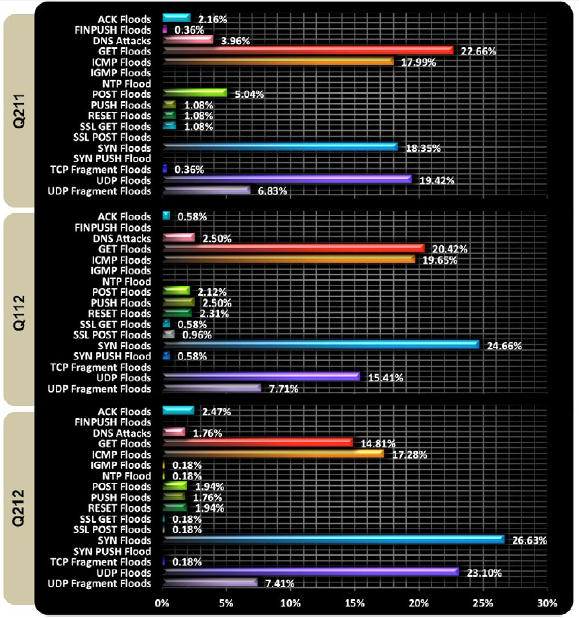
A DDoS attack represents a nightmare for all those all companies that provide web services that could be blocked by similar offensive, let’s imagine the effect of a DDoS against a financial institution or against an e-commerce site of a great on-line store … no doubt the event is synonymous of loss of money. The cyber threat has no boundaries and has hit all the sector of industry such as financial services, e-Commerce, SaaS, payment processing, travel/hospitality and gaming. We learned that a DDoS attack could use different platforms and interesting several infrastructure layers, the detected events have mostly impacted Layer 3 and Layer 4. The Prolexis reports describes the phenomenon as a return to the past, when these layers were the most impacted and the attacks interested principally bandwidth capacity and routing infrastructure. But many company have been hit by multi-vector DDoS attacks, a trend that is increased in the last months and that is the evidence of a significant escalation made by attackers, according Arbor firms around 27% of its customers have experienced the combination of offensive. Infrastructure attacks accounted for 81% of total attacks during the quarter with application layer attacks making up the remaining 19%, data in opposition with what has been observed in the three previous quarters.
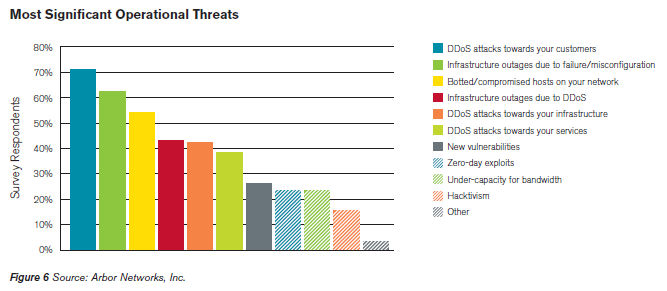
The type of DDoS most used is SYN Flood but it has been also observed a new raise of UDP Floods mode. Interesting parameters for the qualification of a DDoS attack are the duration and Average attack speed. In Q2 2012 the average attack duration, compared with of the previous quarter data, is passed from 28,5 hours to 17 hours and also the average attack speed is decreased recording a speed of 4.4 Gbps and average packet-per-second (pps) volume totaled 2.7 million. Analyzing in detail the number of attacks related to the quarter it’s is anyway notice a reduction of the total number respect previous quarter, it’s also possible observe that 47% of attacks has been registered on June, curiously concomitant opening of Euro 2012 soccer tournament, demonstrating that also sporting events have an impact on the internet security. Statistics on the most significant operational threat encountered in the last year shows the prevalence of DDoS attacks against end customers (71%), over 62 percent related to misconfigurations and/or equipment failures as contributing to outages during and meaningful is also the contribute provided by botnets.
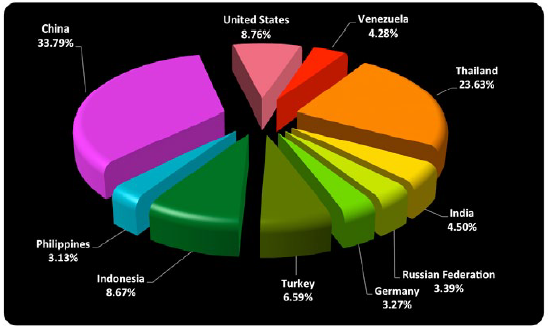
Which are the most active nations under the offensive perspective? This quarter China confirmed its leadership in the chart of attack source country rankings with Thailand and the United States.
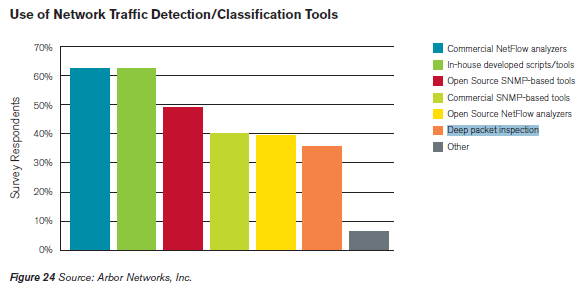
In the next months it is expected that the number of DDoS attacks will still increase also thanks the development of new tools and the diffusion of new botnets. Detection of a DDoS attack Detect a DDoS attack just in time is essential to limit the damage and fight the cyber threat, in literature there are several techniques to identify this phenomena and on the market are available a wide set of network devices that perform the function. Many appliances implements “reputation watch” sentinel that analyze the traffic searching for anomalies in real-time known, trying also to qualify the cyber threat and its origin, as we have introduced the malicious traffic could be generated by automated botnet, trying to ban bad IP addresses ‘on-the-fly’. Many systems are able to dynamic provide an automatic changing in the network context to block incoming malicious traffic and also are able to apply discriminant on it based on the country of origin. Which are the principal device used to mitigate DDoS Attacks? On the market there are several appliance used to limit the damages caused by similar attacks, following a short list of systems using for DDoS detection:
- NetFlow analyzers – The NetFlow protocol is a network protocol developed by Cisco Systems to collecting IP traffic information and it is recognized as a standard for traffic analysis. Network devices (e.g. Routers) that support NetFlow are able to collect IP traffic providing detailed statistics. The component that perform traffic analysis in the NetFlow architecture is named “collector” and usually is implemented by a server. Cisco standard NetFlow version 5 defines a flow as an unidirectional sequence of packets that all share of the following 7 values (Ingress interface (SNMP ifIndex), Source IP address, Destination IP address, IP protocol, Source port for UDP or TCP, Destination port for UDP or TCP, IP Type of Service).Anayzing in automated way the flow is possible to detect in real time a DDoS event localizing the sources of attacks.
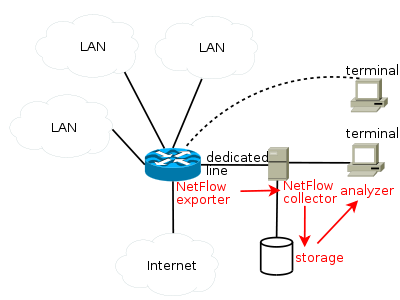
- SNMP-based tools – SNMP-based tools are used by network administrators to collect traffic from network devices like a switch or a router supporting SNMP protocol. As usual these tools consist of two components. One, namely the collector, is to collect SNMP data, and the other, the “grapher”, is to generate HTML formatted output containing traffic loading image which provides a live and visual representation of the network status and traffic trends. These traditional SNMP-based traffic monitoring tools are really effective to detect traffic anomalies, such as an unexpected increase, that may indicate an ongoing attack. From a security perspective collected data sometimes might be either too coarse to detect anomaly and need further analysis.
- Deep packet inspection – DPI devices perform deep packet filtering examining both the data part header of packets composing the traffic once the pass an inspection point. The DPIs may be used for different purposes for example to search for protocol non-compliance, viruses, spam, intrusions and attack detection. A DPI configured in the proper mode would detect the DDoS packets and filter them out.
In the following graph is reported their engage according the report provided by Arbor Networks, with classic Commercial Network Analyzers it is possible to note that are increasing the number of open source system used to mitigate the attacks.
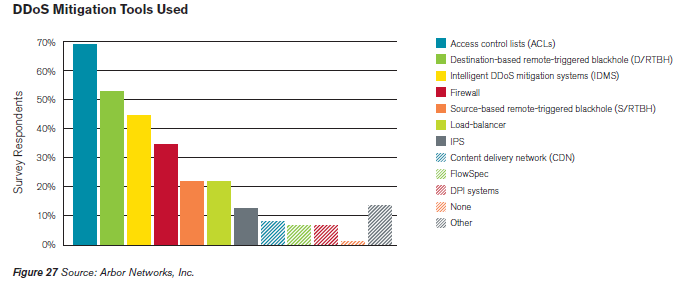
Once Detected the attack it is necessary to apply the proper action to mitigate its operation, and despite their functional and operational limitations, according the principal security firms, ACLs continue to be the most widely used tool to mitigate DDoS attacks. Other possible methods to mitigate a DDoS attack are Intelligent DDoS mitigation systems (IDMS), Destination-based remote triggered blackhole (D/RTBH) a filtering technique that provides the ability to drop undesirable traffic before it enters a protected network and Source-based remote triggered blackhole (S/RTBH) technique allows an ISP to stop malicious traffic on the basis of the source address it comes from and FlowSpec. Following the graph related to data published in the last reports of the Arbor Networks Firm:
Majority of organization have implemented best current practices (BCPs) in critical network infrastructure security, and according the various reports provided by different security firms the level of awareness and the efficiency of the response to the incident is increased obtaining meaning progress over last years. These principal BCPs implemented are:
- Authentication for BGP, IGPs
- Separate out-of-band (OOB) management network
- iACLs at network edges
- BCP38/BCP84 anti-spoofing at network edges
A Look to the future … concerns related IPv6
One of the factor that will impact the evolution of DDoS attacks is the introduction of IPv6 protocol. The expert are convinced that DDoS attack could be strengthened around 90% in IPv6 when compared to the IPv4. According SANS Institute the path taken by the attack packets can be either one way (TCP, UDP and other attacks) or two ways (ICMP traffic). Technically IPv6 introduces six optional headers such as Routing header that could be used to force a packet transit on through routers, making possible that the attack packets could transit between the routers endlessly suturing the network with forged packets and can lead to a powerful DDoS attack. IPv6 has also another powerful feature that could be exploited, the mobile IP that has been introduced in the last version of the protocol to allow a user to change his geographical location moving to different networks maintaining a single IP address. This is achieved by the extension headers provided in IPv6. The original IPv6 address is stored in the extension header whereas an additional temporary address is maintained in the IP header. The temporary address keeps changing when the user is mobile but the original IP address remains unchanged. An attacker can easily change this temporary IP address and carry out spoof attacks.
Conclusions
This type of attacks is still preferred by group of hacktivist that are intensifying the offense against private companies and governments, but also cybercrime is adopting it in complex operation where the need is to block a web service meanwhile a fraud schema is implemented. The attacks is also largely adopted in cyber warfare to hit the critical infrastructures of a country, let’s remind that also financial institution of a nation are considerable vital entities for a country. Despite the last quarter has registered a reduction of the total number of attacks the cyber threat is still very worrying, the DDoS doubled in Q2 2012 respect the same quarter one year ago. The diffusion of botnets and also the introduction of IPv6 represents a further factors that could amplify the magnitude of the cyber threats and frequency of this type of attacks. DDoS attack is evolving, are both private and government sectors ready to protect their structures? Underestimate the threat could be very dangerous!
Pierluigi Paganini

No comments:
Post a Comment