https://www.howtoforge.com/tutorial/how-to-safely-wipe-your-data
Sometimes, we need to completely and irreversibly wipe all data contained in a disk to keep them from falling into the wrong hands. This may not be something we are doing on a day to day basis, but if you want to do it, you should do it right and ensure that the data cannot be recovered by experts. One of the many ways of doing this is through Darik's Boot and Nuke bootable live CD. This tool is made from the same team that develops the professional-grade Blancco data eraser, only it is available for free and without guarantee or support. The reason I like DBaN is because it is very simple to use and does the job fast.
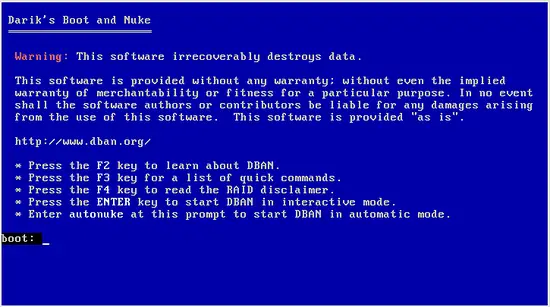
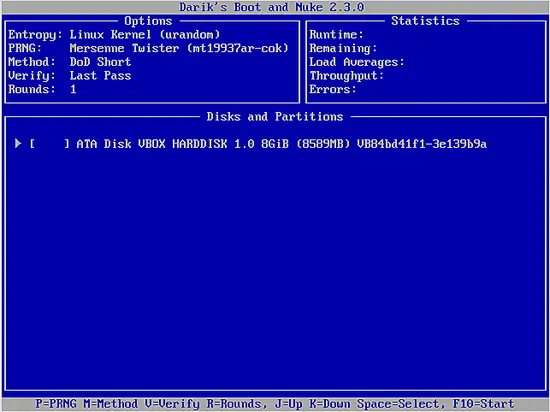
Press “Enter” to start the software in interactive mode. This will bring you to the next step which is to choose the disk/partition you want to wipe. In the following screenshot, you will only see one disk as I am running this in a Virtual Machine.
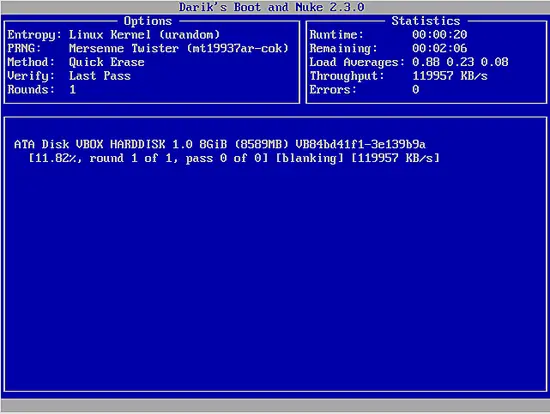
If you have more partitions, you can navigate between the entries with “J” and “K” which correspond to up and down, and press “Spacebar” to select which ones you want to wipe. When you're done with this, you may hit “F10” and the wiping process will initiate.
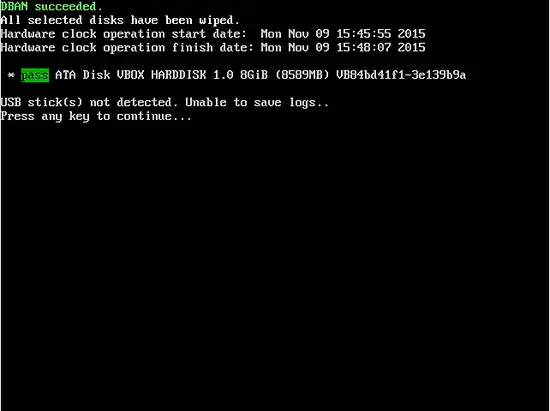
Note that if you have followed this standard procedure, DBaN utilized the DoD 5220.22-M methodology to wipe your disks. This however isn't the only way you can erase your data with DBaN.
Here is an overview of the main data erasing methods and which one is suitable for your purpose.
DoD 5220
This is the default method of choice of DBaN. It basically overwrites all addressable locations in the disk with seven passes of random characters so that the previously contained data isn't recoverable. This is the methodology used by the US Department of Defense, so it is a safe and tested choice for most applications.
OPS-II
This methodology suggests multiple passes of writing zero's and one's in the disk until it finally writes a random character. This ensures that the procedure cannot be reverse-engineered and the wiped data can't be recovered.
Gutmann
The Gutmann method is the one that uses the greater number of passes onto the region to be erased. More specifically, it applies 27 random-order passes and eight passes using random data. For this reason, this choice may take more time compared to the others, but it is generally considered very safe.
PRNG
This method utilizes a pseudo-random number generator to overwrite the erased region with seemingly random characters. All is done in one-pass, so it is quite quick and safe enough for home and small office use.
Quick
This method is simply filling your to be erased disk with zeros. It is the fastest and least safe method, but it will cover most simple purposes.
Sometimes, we need to completely and irreversibly wipe all data contained in a disk to keep them from falling into the wrong hands. This may not be something we are doing on a day to day basis, but if you want to do it, you should do it right and ensure that the data cannot be recovered by experts. One of the many ways of doing this is through Darik's Boot and Nuke bootable live CD. This tool is made from the same team that develops the professional-grade Blancco data eraser, only it is available for free and without guarantee or support. The reason I like DBaN is because it is very simple to use and does the job fast.
Boot and Nuke
To use DBaN, download the .iso file from the official website and burn it on a CD or USB drive. Then boot from it and you will get a screen with some basic options.Press “Enter” to start the software in interactive mode. This will bring you to the next step which is to choose the disk/partition you want to wipe. In the following screenshot, you will only see one disk as I am running this in a Virtual Machine.
If you have more partitions, you can navigate between the entries with “J” and “K” which correspond to up and down, and press “Spacebar” to select which ones you want to wipe. When you're done with this, you may hit “F10” and the wiping process will initiate.
Note that if you have followed this standard procedure, DBaN utilized the DoD 5220.22-M methodology to wipe your disks. This however isn't the only way you can erase your data with DBaN.
Data Wiping Methods
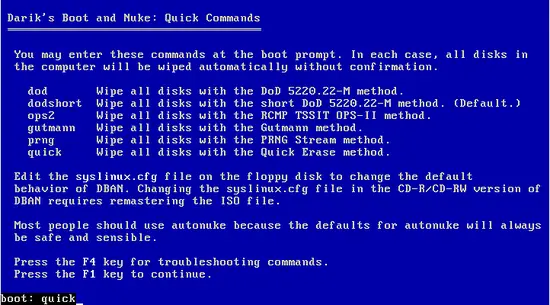
While in the main screen, press “F3” to get the list of commands. You may type one of the six commands and press “F1” to continue with the selected data erasing method.Here is an overview of the main data erasing methods and which one is suitable for your purpose.
DoD 5220
This is the default method of choice of DBaN. It basically overwrites all addressable locations in the disk with seven passes of random characters so that the previously contained data isn't recoverable. This is the methodology used by the US Department of Defense, so it is a safe and tested choice for most applications.
This methodology suggests multiple passes of writing zero's and one's in the disk until it finally writes a random character. This ensures that the procedure cannot be reverse-engineered and the wiped data can't be recovered.
Gutmann
The Gutmann method is the one that uses the greater number of passes onto the region to be erased. More specifically, it applies 27 random-order passes and eight passes using random data. For this reason, this choice may take more time compared to the others, but it is generally considered very safe.
PRNG
This method utilizes a pseudo-random number generator to overwrite the erased region with seemingly random characters. All is done in one-pass, so it is quite quick and safe enough for home and small office use.
Quick
This method is simply filling your to be erased disk with zeros. It is the fastest and least safe method, but it will cover most simple purposes.

No comments:
Post a Comment