http://www.cyberciti.biz/faq/how-to-find-out-aes-ni-advanced-encryption-enabled-on-linux-system
The Intel Advanced Encryption Standard (AES) or New Instructions (AES-NI) engine enables extremely fast hardware encryption and decryption for openssl, ssh, vpn, Linux/Unix/OSX full disk encryption and more. How do I check support for Intel or AMD AES-NI is loaded in my running Linux in my Linux based system including openssl?
The Advanced Encryption Standard Instruction Set (or the Intel Advanced Encryption Standard New Instructions - "AES-NI") allows certain Intel/AMD and other CPUs to do extremely fast hardware encryption and decryption. "AES-NI" is an extension to the x86 instruction set architecture for microprocessors from Intel and AMD. It increases the speed of apps performing encryption and decryption using the AES. Several server and laptop vendors have shipped BIOS configurations with the AES-NI extension disabled. You may need a BIOS update to enable them or change the BIOS settings. The following CPUs are supported:
Type the following command to make sure that the processor has the AES instruction set and enabled in the BIOS:
OR
Sample outputs:
The aes output indicates that I have the AES-NI support enabled by Linux.
And:
Sample outputs:
Sample outputs from VIA based cpu that supports the AES:
And:
OR
The Intel Advanced Encryption Standard (AES) or New Instructions (AES-NI) engine enables extremely fast hardware encryption and decryption for openssl, ssh, vpn, Linux/Unix/OSX full disk encryption and more. How do I check support for Intel or AMD AES-NI is loaded in my running Linux in my Linux based system including openssl?
The Advanced Encryption Standard Instruction Set (or the Intel Advanced Encryption Standard New Instructions - "AES-NI") allows certain Intel/AMD and other CPUs to do extremely fast hardware encryption and decryption. "AES-NI" is an extension to the x86 instruction set architecture for microprocessors from Intel and AMD. It increases the speed of apps performing encryption and decryption using the AES. Several server and laptop vendors have shipped BIOS configurations with the AES-NI extension disabled. You may need a BIOS update to enable them or change the BIOS settings. The following CPUs are supported:
- Intel Westmere/Westmere-EP (Xeon 56xx)/Clarkdale (except Core i3, Pentium and Celeron)/Arrandale(except Celeron, Pentium, Core i3, Core i5-4XXM).
- Intel Sandy Bridge cpus (except Pentium, Celeron, Core i3).
- Intel mobile Core i7 and Core i5.
- Intel Ivy Bridge processors All i5, i7, Xeon and i3-2115C only.
- Intel Haswell processors (all except i3-4000m, Pentium and Celeron).
AMD Bulldozer/Piledriver/Steamroller/Jaguar/Puma-based processors. - AMD Geode LX processors.
- VIA PadLock (a different instruction set than Intel AES-NI but does the same thing at the end of the day).
- ARM - selected Allwinner and Broadcom using security processor. There are few more ARM based processor.
How do I find out that the processor has the AES/AES-NI instruction set?
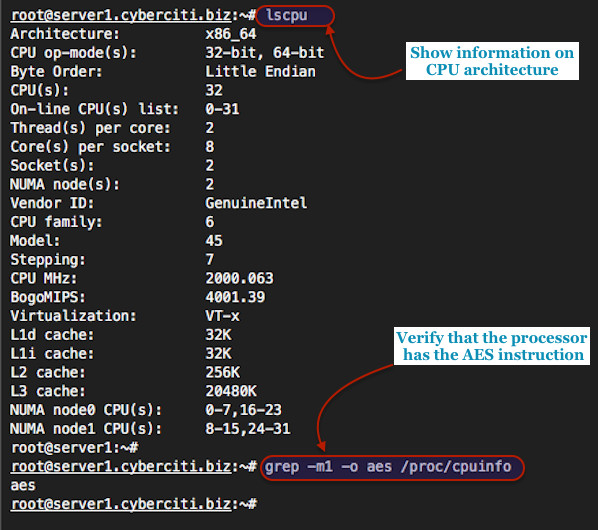
To find out cpu type and architecture type:# lscpuType the following command to make sure that the processor has the AES instruction set and enabled in the BIOS:
# grep -o aes /proc/cpuinfoOR
# grep -m1 -o aes /proc/cpuinfoSample outputs:
The aes output indicates that I have the AES-NI support enabled by Linux.
How do I verify that all my CPU supports AES NI?
The output of the following two commands should be same:# lscpu | grep '^CPU(s):'
32And:
# grep -o aes /proc/cpuinfo | wc -l
32Is Intel AES-NI instructions optimized driver loaded for my Linux server/laptop/desktop?
Type the following command:# sort -u /proc/crypto | grep moduleSample outputs:
module : aesni_intel
module : aes_x86_64
module : crc32_pclmul
module : crct10dif_pclmul
module : ghash_clmulni_intel
module : kernel
Is Intel AES-NI enabled for openssl enabled?
Now that we have verified support, it's time to test it. Is my AES-NI/VIA padlock engine supported?$ openssl engine Sample outputs from VIA based cpu that supports the AES:
(padlock) VIA PadLock (no-RNG, no-ACE)
(dynamic) Dynamic engine loading support
Another output from Intel based system that support the AES-NI:$ openssl engine
(aesni) Intel AES-NI engine
(dynamic) Dynamic engine loading supportTest: AES-NI CPU vs Normal CPU without the AES-NI/Packlock support
In this example, serverA has the AES-NI and serverB has no support for hardware encryption:$ dd if=/dev/zero count=1000 bs=1M | ssh -l vivek -c aes128-cbc serverA "cat >/dev/null"
Password:
1000+0 records in
1000+0 records out
1048576000 bytes (1.0 GB) copied, 10.6691 s, 98.3 MB/sAnd:
$ dd if=/dev/zero count=1000 bs=1M | ssh -l vivek -c aes128-cbc serverB "cat >/dev/null"
vivek@localhost's password:
1000+0 records in
1000+0 records out
1048576000 bytes (1.0 GB) copied, 31.6675 s, 33.1 MB/sTest: How do I benchmark my openssl performance?
Again run the following commands on both the systems:# openssl speedOR
# openssl speed aes-128-cbcPopular Linux or Unix/BSD applications that can benefit from the AES-NI from high speed ecryption/decryption
- dm-crypt for full-disk encryption on Linux.
- 7-Zip app.
- Google chrome and firefox browsers
- FreeBSD's OpenCrypto API i.e aesni driver for zfs and other file systems.
- OpenSSL 1.0.1 and above.
- TrueCrypt 7.0 and above or VeraCrypt.
- Citrix XenClient 1.0 and above.
- Compilers such as GCC 4.4+, Intel C/C++ compiler 11.1+, Clang 3.3+ and more.
- Libraries for golang, java, NSS, openssl and more.
- Linux and BSD firewalls and vpn especially easy to use pfsense, ipcop and more.
- Operating system based on Linux, *BSD, Unix, Microsoft, Android, iOS, Apple OS X and more.

No comments:
Post a Comment